Introduction
As I continue building my cloud security skillset, I’ve been exploring foundational AWS services that underpin effective security architecture. One of the most critical services is AWS IAM (Identity and Access Management), which controls who can access your AWS resources and what specific actions they can perform.
In this blog post, I’ll share my experience implementing a secure access control solution using AWS IAM. I created customized policies, configured user groups, and established permission boundaries to enforce the principle of least privilege, demonstrating how IAM serves as the cornerstone of AWS security.
Project Overview
Time Investment: Approximately 4 hours (including research, setup, policy creation, testing and validation)
AWS Services Used:
- AWS Identity and Access Management (IAM)
- Amazon EC2 (for permission testing)
Key Concepts Learned:
- JSON policy structure and syntax
- Resource tagging for dynamic permissions
- IAM user and group management
- Policy testing and simulation
- Least privilege implementation
Why AWS IAM is Foundational to Cloud Security
Before diving into implementation, here’s why IAM is considered the cornerstone of AWS security:
- Fine-Grained Access Control: Define precise permissions for each user or system
- Identity Federation: Integrate with existing identity providers for centralized authentication
- Temporary Credentials: Issue short-lived credentials for enhanced security
- Multi-Factor Authentication: Enforce additional verification layers
- Zero Trust Foundation: Build security from identity rather than network perimeter
Step 1: Understanding Resource Organization with Tags
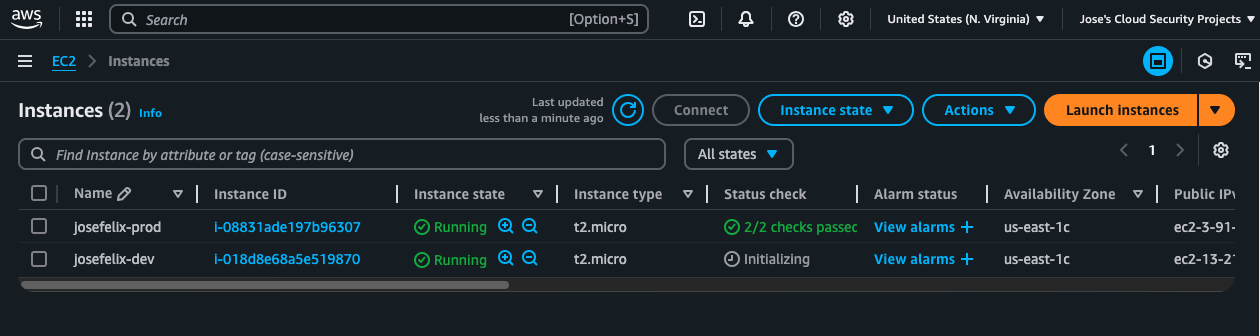
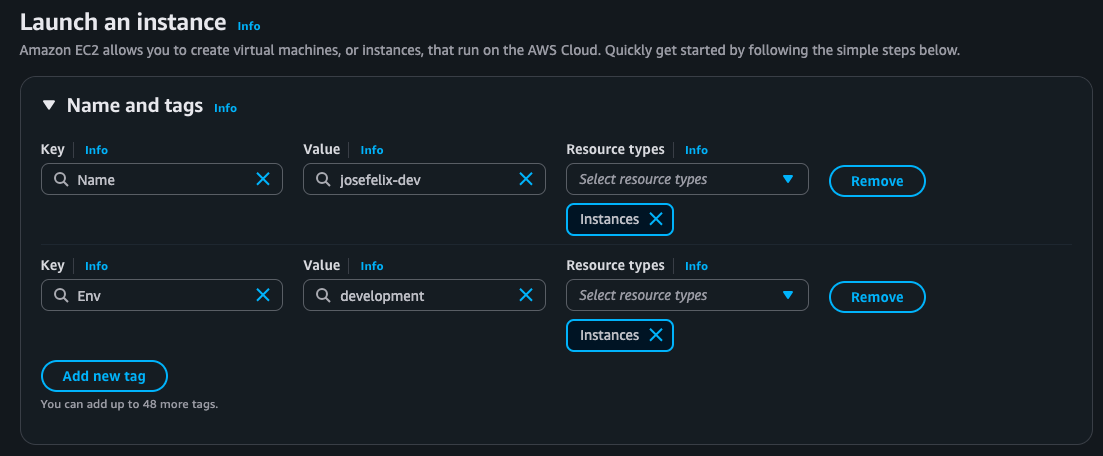
Tags are a powerful way to organize AWS resources and apply permissions dynamically. For this project:
- Created EC2 instances tagged with “Env” to distinguish environments
- Set “Env” tag values as “production” and “development”
- Planned permission scheme based on these resource designations
This tagging strategy enables attribute-based access control (ABAC), where permissions automatically apply to resources based on their tags rather than requiring explicit resource IDs in policies.
Security Impact: Resource tagging creates a scalable permission system that continues to work as your infrastructure grows, without needing constant policy updates for new resources.
Step 2: Creating IAM Policies
The central component of this project was crafting a custom IAM policy that implemented least privilege access. I created a JSON policy that:
- Allows full EC2 permissions on resources tagged “Env=development”
- Permits viewing (describing) information for all EC2 instances
- Explicitly denies the ability to create or delete tags on any instances
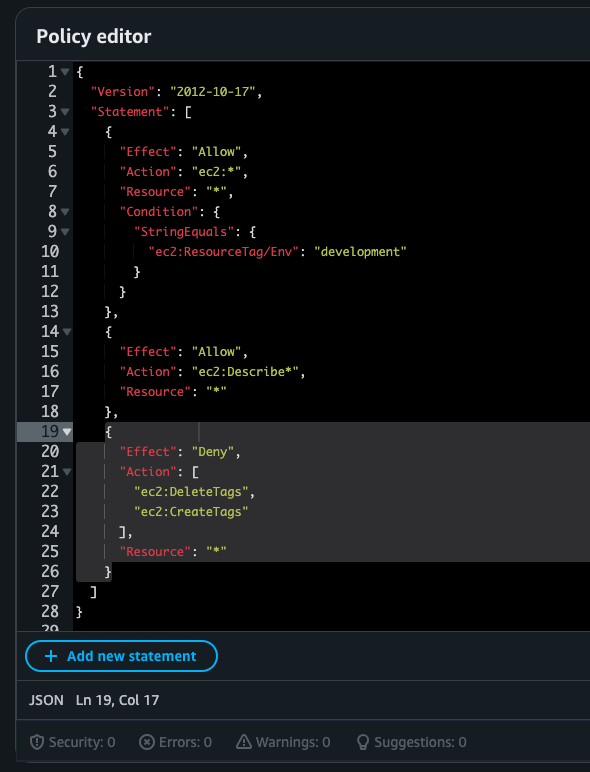
Understanding how these policy statements interact was crucial:
- The first statement grants broad permissions but only for development resources
- The second statement allows read-only access to all instances for visibility
- The third statement creates an explicit deny for tag manipulation, which always takes precedence
Policy Structure Insight: AWS policies evaluate multiple statements to determine access, with explicit deny statements always overriding allow statements.
Here’s the complete policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "ec2:*",
"Resource": "*",
"Condition": {
"StringEquals": {
"ec2:ResourceTag/Env": "development"
}
}
},
{
"Effect": "Allow",
"Action": [
"ec2:Describe*"
],
"Resource": "*"
},
{
"Effect": "Deny",
"Action": [
"ec2:CreateTags",
"ec2:DeleteTags"
],
"Resource": "*"
}
]
}Step 3: Setting Up Account Alias
To improve usability, I created a custom AWS account alias:
- Created the account alias “josefelix-alias-company”
- Verified the new sign-in URL: https://josefelix-alias-company.signin.aws.amazon.com/console
- Documented the improved user experience for team members
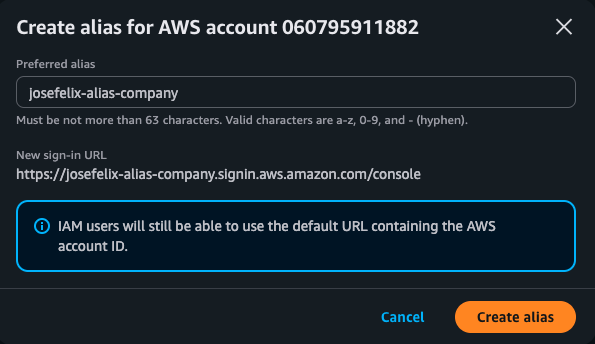
Security Impact: While primarily a usability feature, customized sign-in URLs help users identify the correct account, reducing the chance of accessing the wrong environment.
Step 4: Creating IAM Users and User Groups
Rather than assigning policies directly to individual users, I followed security best practices by:
- Creating a development user group for team members
- Attaching the custom policy to the group
- Adding users to the group to automatically inherit permissions
- Setting up temporary credentials with password rotation requirements
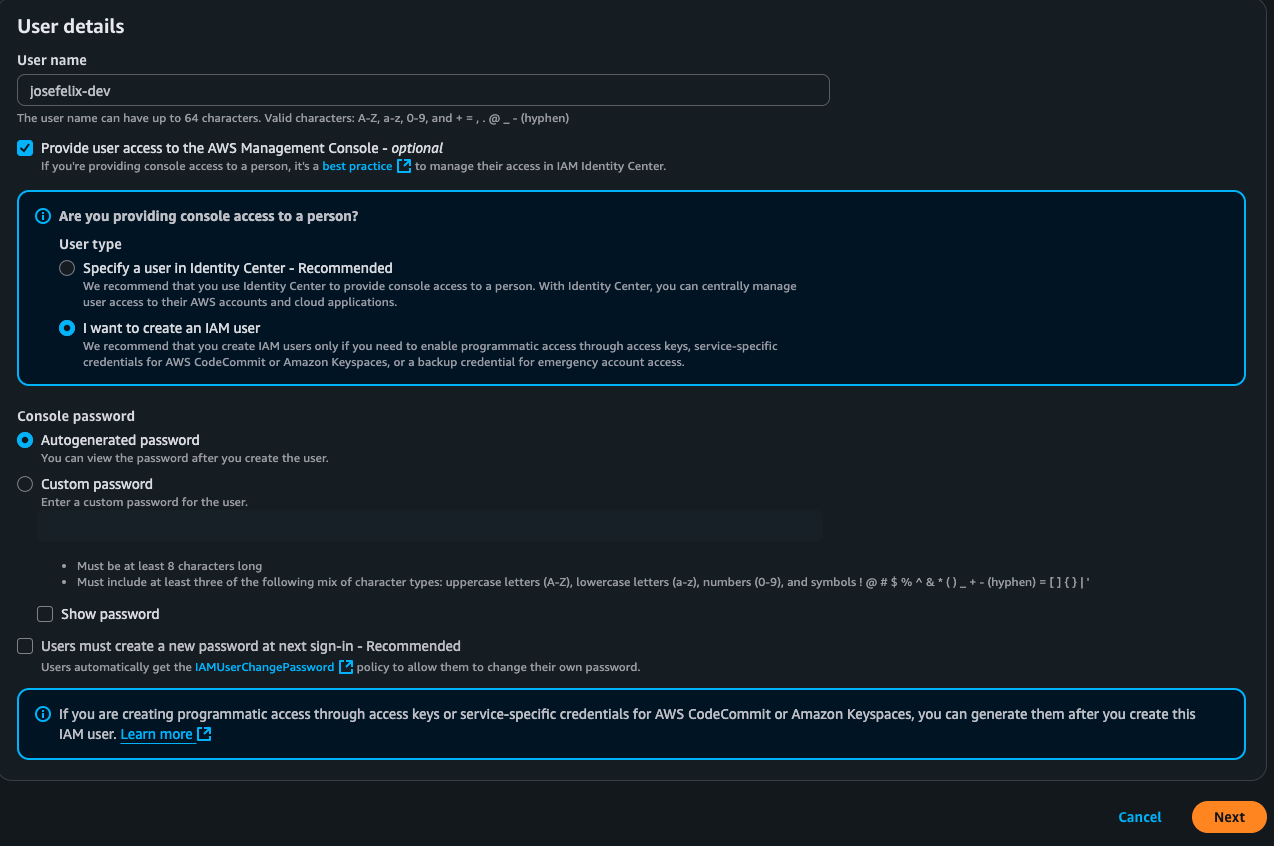
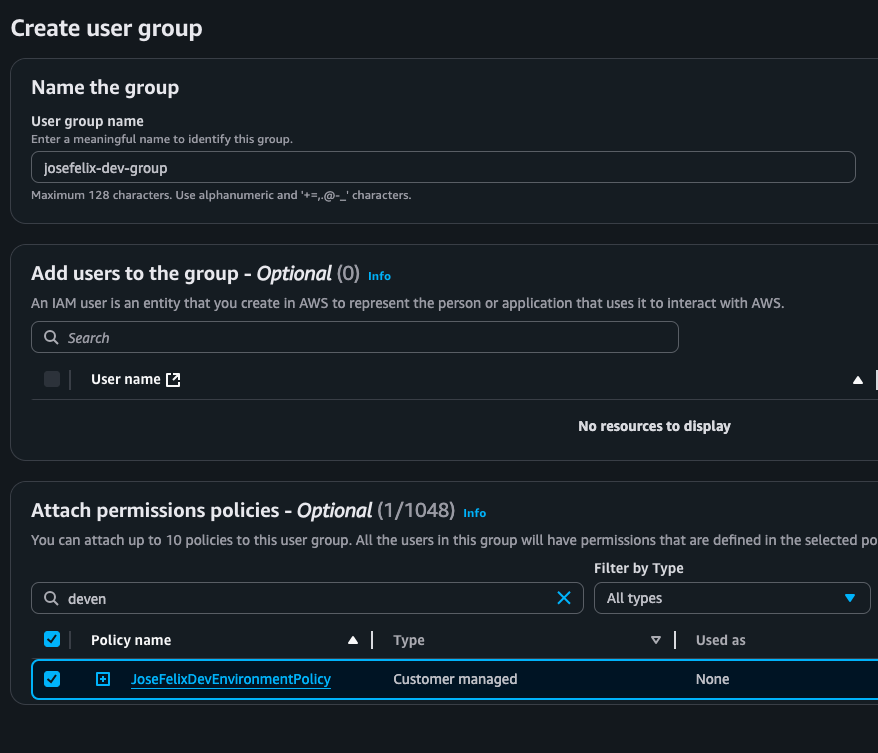
Security Impact: Group-based permission assignment significantly reduces administrative overhead and ensures consistent permissions across similar users, minimizing the risk of permission discrepancies.
Step 5: Testing IAM Policies
To verify my policy implementation, I conducted testing:
- Attempted to stop a production instance (Result: Access Denied)
- Attempted to stop a development instance (Result: Successfully Stopped)
- Attempted to modify tags on either instance (Result: Access Denied)
- Verified ability to view all instance details (Result: Successfully Listed)
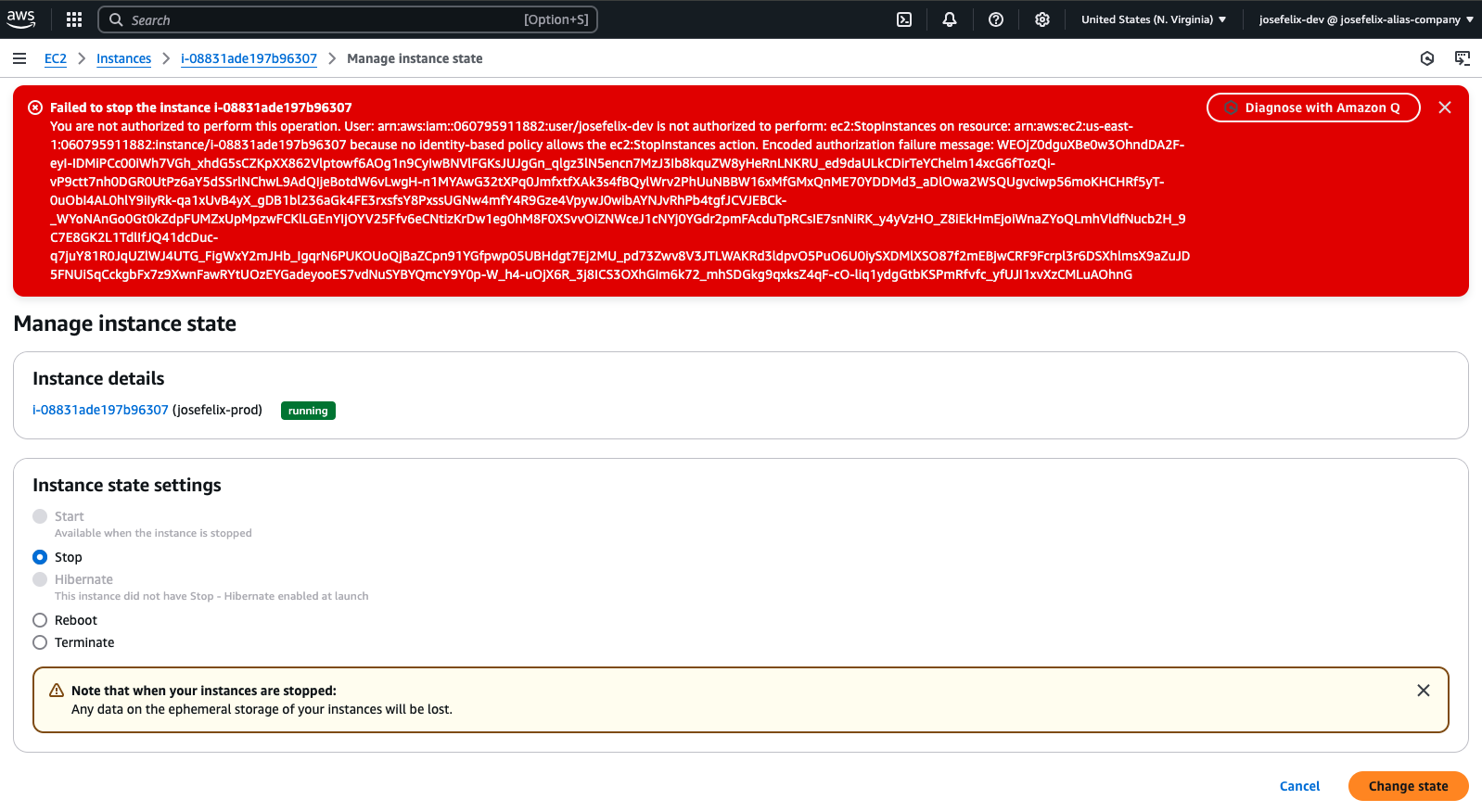
This error message confirms our policy is working correctly – the user can’t stop the production instance because it doesn’t have the “Env=development” tag.
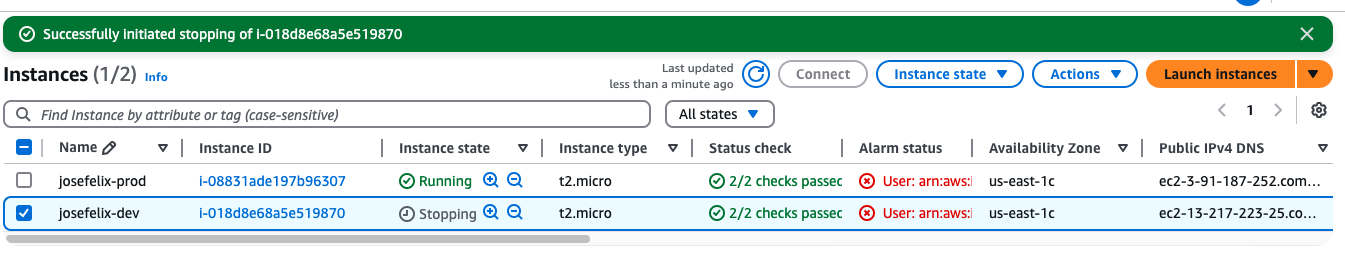
This confirmation message shows the policy correctly allows operations on development instances.
Testing Insight: Policy testing should verify both what actions are allowed AND what actions are explicitly denied to ensure complete coverage.
Step 6: Using the IAM Policy Simulator
For more advanced testing without affecting production resources, I utilized the IAM Policy Simulator:
- Set up a simulation for the development user group
- Tested StopInstances and DeleteTags actions
- Initially saw both actions denied
- Adjusted simulation to specify an EC2 instance with the development tag
- Confirmed StopInstances was allowed but DeleteTags remained denied
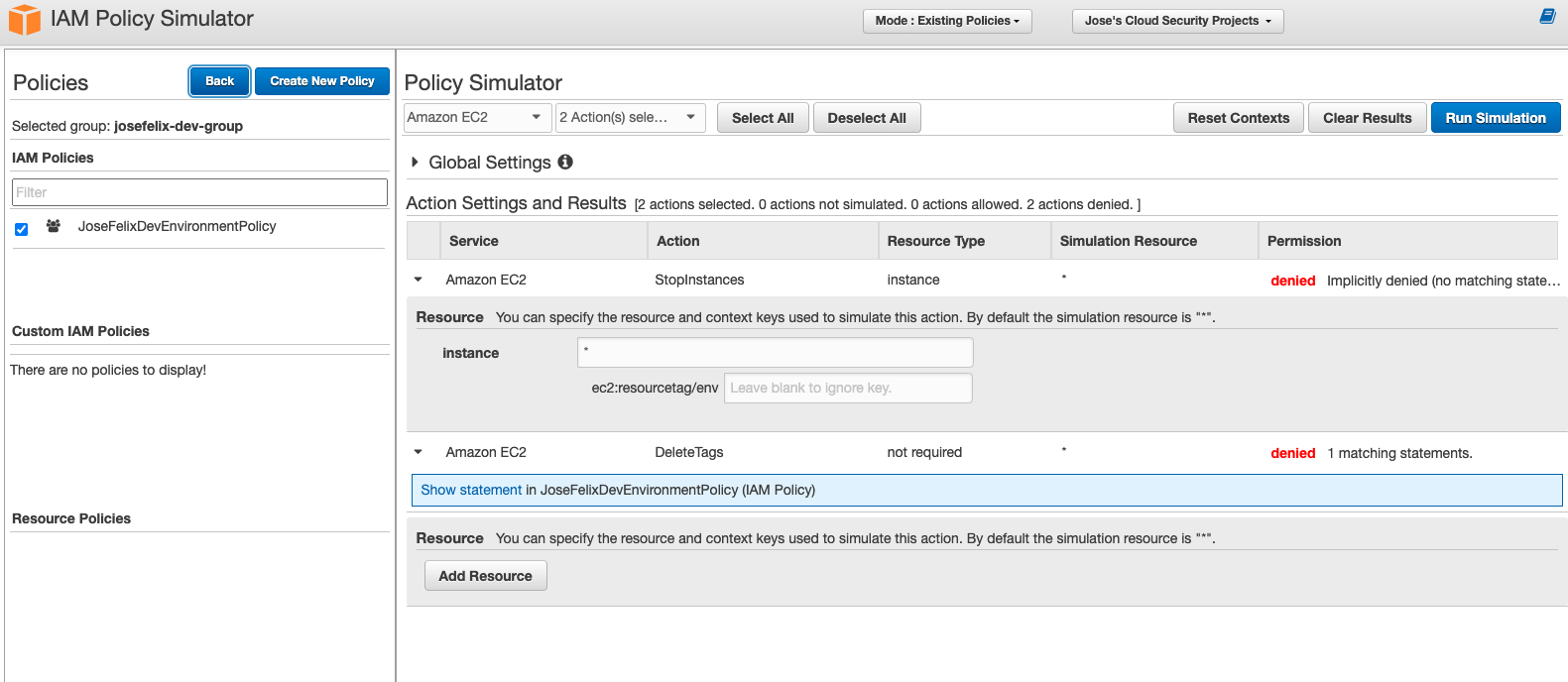
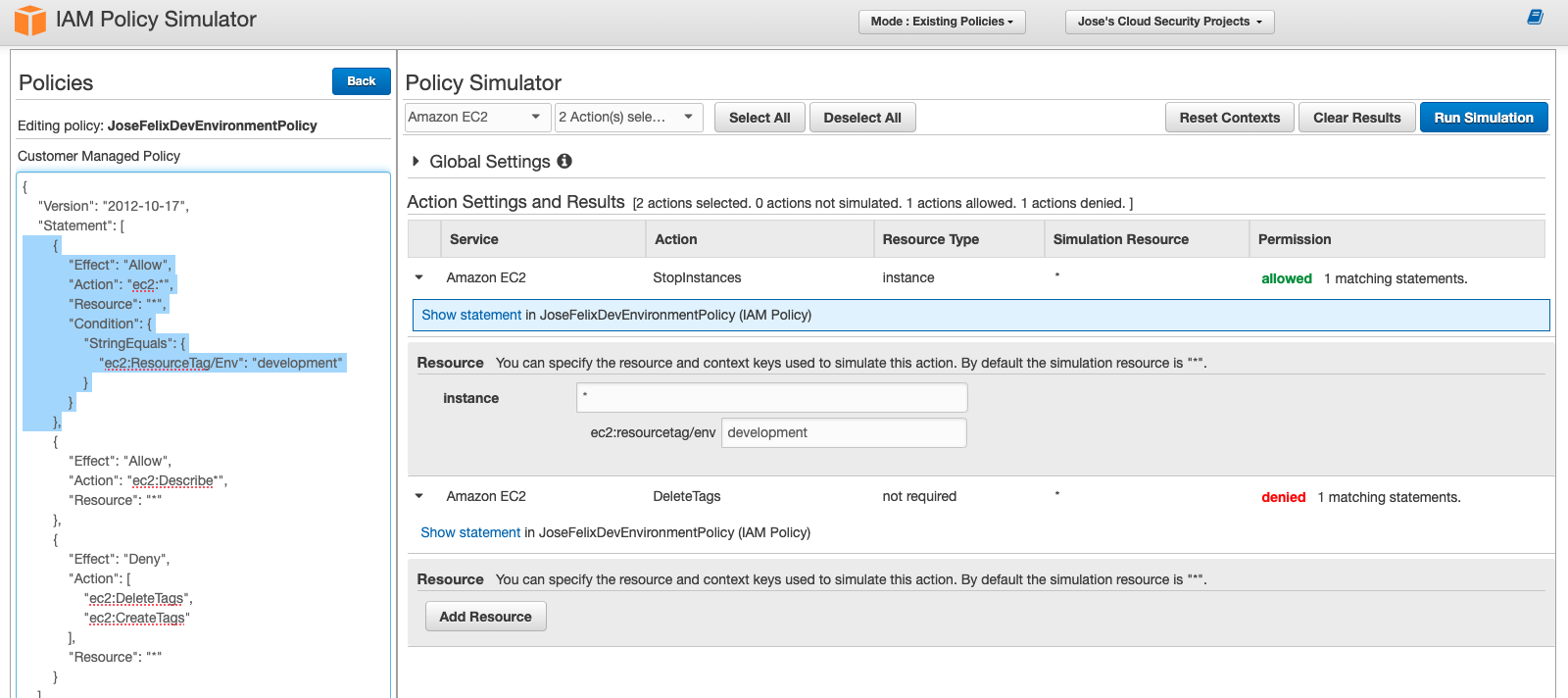
The Policy Simulator proved invaluable for testing complex permission scenarios without risking production impact.
Security Insight: Regular permission validation with the Policy Simulator should be part of security maintenance to ensure policies continue to enforce intended access controls.
Step 7: Documenting Security Controls
The final step involved documenting the implemented security controls:
- Created a permissions reference sheet for administrators
- Documented the tag-based permission structure
- Established procedures for adding new users to appropriate groups
- Created a process for periodically reviewing permissions
Documentation ensures security controls remain understandable and manageable over time.
Business Applications of This Approach
The techniques demonstrated in this project apply to various business scenarios:
Development Team Management
- Separate environments for development, testing, and production
- Prevent developer access to production data or systems
- Allow self-service for development resources
- Implement controlled promotion processes
Contractor Access
- Grant temporary access with specific time limits
- Restrict contractors to only the resources they need
- Prevent modification of security controls
- Enable easy access revocation
Compliance Requirements
- Implement separation of duties for regulated industries
- Create audit trails for access changes
- Enforce principle of least privilege
- Document access controls for compliance auditors
Challenges and Solutions
Challenge 1: Understanding JSON Policy Structure
The policy language can be complex, with various elements like Effect, Action, Resource, and Condition working together.
Solution: I studied AWS documentation and broke down example policies to understand each component. Building policies incrementally helped me validate each part before adding complexity.
Challenge 2: Testing Multi-Level Permissions
Verifying that combinations of Allow and Deny statements work correctly requires systematic testing.
Solution: I developed a test plan that checked each permission boundary and used the Policy Simulator to validate complex scenarios.
Key Takeaways and Best Practices
- Use Tag-Based Access Control: Tags provide flexible, scalable permission management without hardcoding resource IDs.
- Implement Least Privilege: Start with minimal permissions and add only what’s required.
- Prefer Groups Over Individual Permissions: Assign permissions to groups rather than individual users for consistency.
- Test Before Implementing: Use the Policy Simulator to verify policies before applying them to production.
- Document Your Permission Structure: Maintain clear documentation of your permission model for onboarding and auditing.
Cost Management Tip: IAM itself is free, but the resources you control with IAM may have costs associated with them. Always be aware of what resources users have permission to create or modify.
Applying These Concepts to Security Architecture
This IAM implementation demonstrates several security architecture principles:
- Defense in Depth: Multiple permission layers protect critical resources
- Principle of Least Privilege: Users receive only the permissions they need
- Separation of Duties: Different access levels prevent single-person control
- Operational Security: Processes ensure permissions remain current and appropriate
Each of these principles contributes to a robust security posture that protects AWS environments from both accidental and intentional harmful actions.
What’s Next?
Building on this IAM foundation, my upcoming security projects will explore:
- Encrypting sensitive data with AWS KMS
- Implementing automated threat detection with GuardDuty
- Managing secrets securely with AWS Secrets Manager
- Building a Virtual Private Cloud (VPC)
Each of these projects will leverage the secure access foundation established through IAM to ensure only authorized users can access sensitive security functions.
Conclusion
Implementing secure access control with AWS IAM was a valuable learning experience that demonstrated the importance of identity-based security in cloud environments. The ability to create fine-grained, tag-based permissions and apply them consistently through groups forms the foundation of AWS security architecture.
As a US Navy veteran transitioning into Cloud Security, I found this project particularly relevant because it mirrors military security principles: carefully controlled access, need-to-know permissions, and layered protection mechanisms. These universal security concepts translate perfectly to cloud environments.
Have you implemented IAM in your AWS environment? What challenges did you encounter with permission management? Let me know in the comments below!
Stay tuned for my upcoming projects as I continue building expertise in AWS security services.