As I continue building my cloud security skillset, I’ve been exploring more advanced aspects of AWS VPC security best practices that are essential for creating truly secure cloud environments. Building on my previous project where I created a basic VPC, this post delves deeper into configuring the actual traffic flow and security controls within that network infrastructure.
In this blog post, I’ll share my experience implementing comprehensive security controls for AWS Virtual Private Cloud (VPC) environments. I configured route tables to direct traffic, created security groups to protect resources, and set up network ACLs for subnet-level security. I also gained hands-on experience with multi-region deployment using AWS CloudShell and leveraged EC2 Global View to monitor distributed resources from a single dashboard.
This project builds upon my previous AWS work including implementing secure access management with AWS IAM, creating interactive dashboards with QuickSight, and hosting static websites on S3. Each of these projects represents another step in building a comprehensive cloud security foundation.
Project Overview
Time Investment:
Approximately 2-3 hours (including configuration, testing, and documentation)
AWS Services Used:
- Route Tables
- Security Groups
- Network ACLs
- AWS CloudShell
- EC2 Global View
Key Concepts Learned:
- Traffic flow management within VPCs
- Multi-layered security controls
- Stateful vs. stateless filtering
- Multi-region deployment strategies
- Centralized resource monitoring
Why VPC Traffic Management Is Critical for Security
Before diving into implementation, here’s why proper traffic management is vital for cloud security:
Defense in Depth:
Multiple security layers create redundant protection against threats
Traffic Isolation:
Control which resources can communicate with each other
Exposure Limitation:
Minimize internet-facing surface area of your infrastructure
Granular Access Control:
Apply different security rules at various levels of your network
Audit and Visibility:
Gain comprehensive understanding of allowed communication paths
Understanding Default VPCs and Their Advantages
AWS automatically creates a default VPC in each region when you create your AWS account. This default VPC comes pre-configured with basic settings that allow you to launch resources immediately without additional network configuration.
The default VPC includes:
- A public subnet in each Availability Zone
- An internet gateway attached to the VPC
- Default security group, network ACL, and route table
- DNS resolution enabled
The main advantages of the default VPC include:
- Immediate Resource Deployment: Launch EC2 instances without additional network configuration
- Public Internet Access: Resources receive public IP addresses and can access the internet
- Regional Isolation: Each region has its own default VPC, providing automatic geographic separation
- Basic Security: Default security groups only allow inbound traffic from resources within the same security group
However, for production workloads and security-sensitive applications, custom VPCs (like the one I’m configuring in this project) provide better isolation, more granular control, and stronger security through proper subnet design and layered security controls.
Step 1: Configuring Route Tables
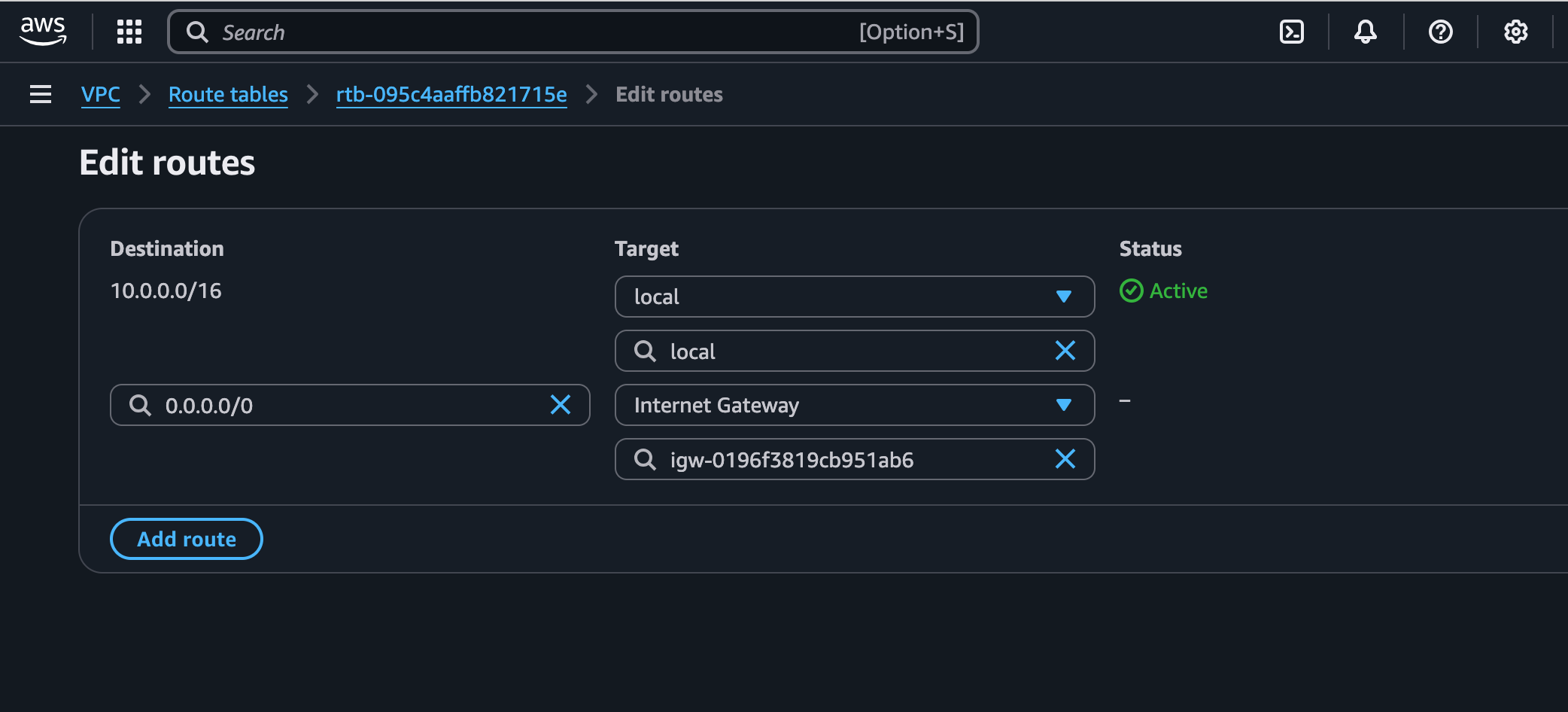
Route tables are sets of rules that determine where network traffic is directed within a VPC. They function like a GPS for data packets, telling them which path to take to reach their destination.
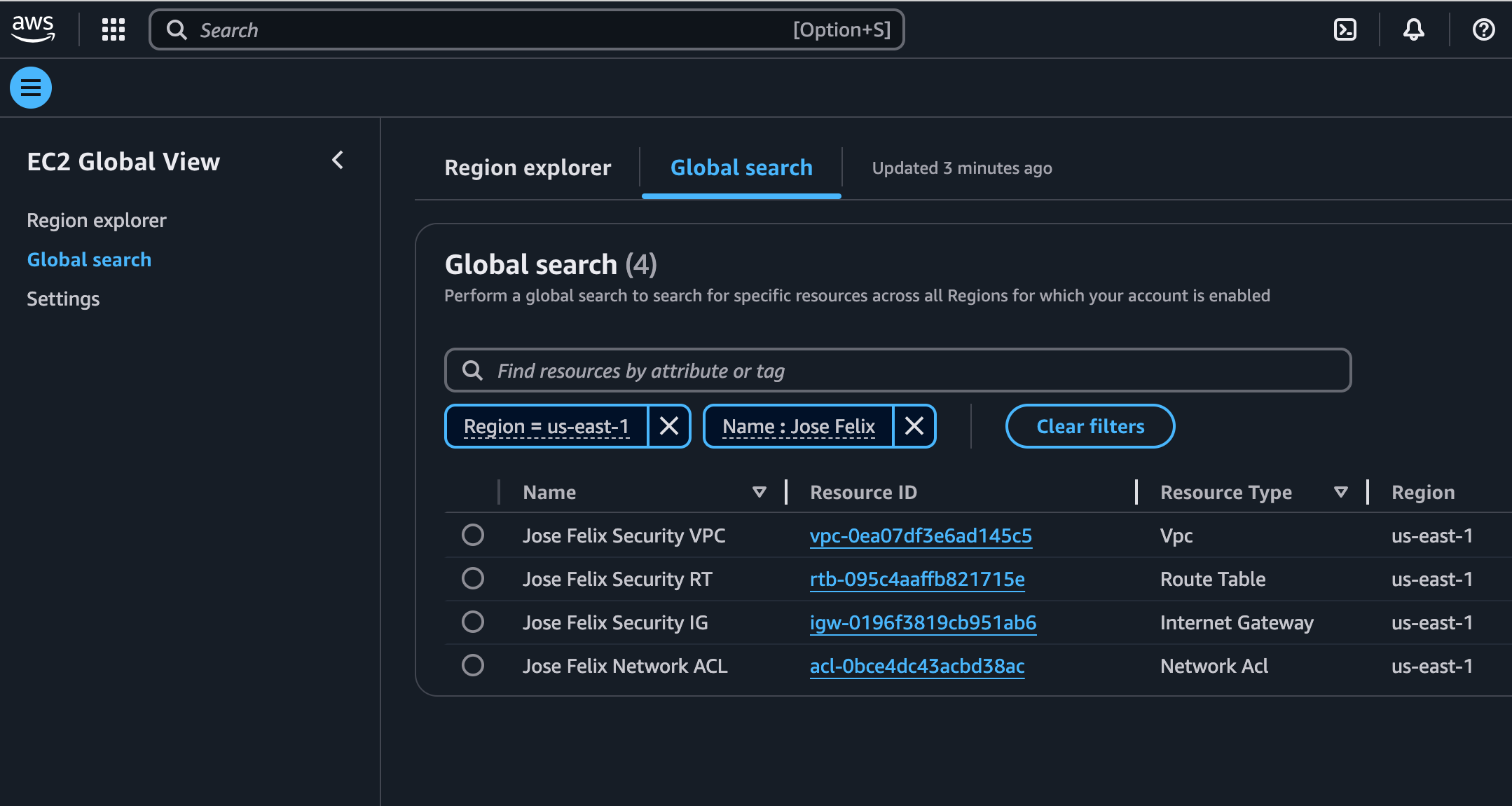
I configured route tables to make my subnets public by establishing a connection between the subnet and the internet gateway. I added a route with a destination of 0.0.0.0/0 and a target of my internet gateway (igw-0196f3819cb951ab6), ensuring that all traffic not destined for the local VPC network would be sent to the internet.
Security Application:
Route tables are foundational for network segmentation, allowing me to control which subnets can access the internet directly and which must remain isolated or route through security appliances.
Step 2: Implementing Security Groups
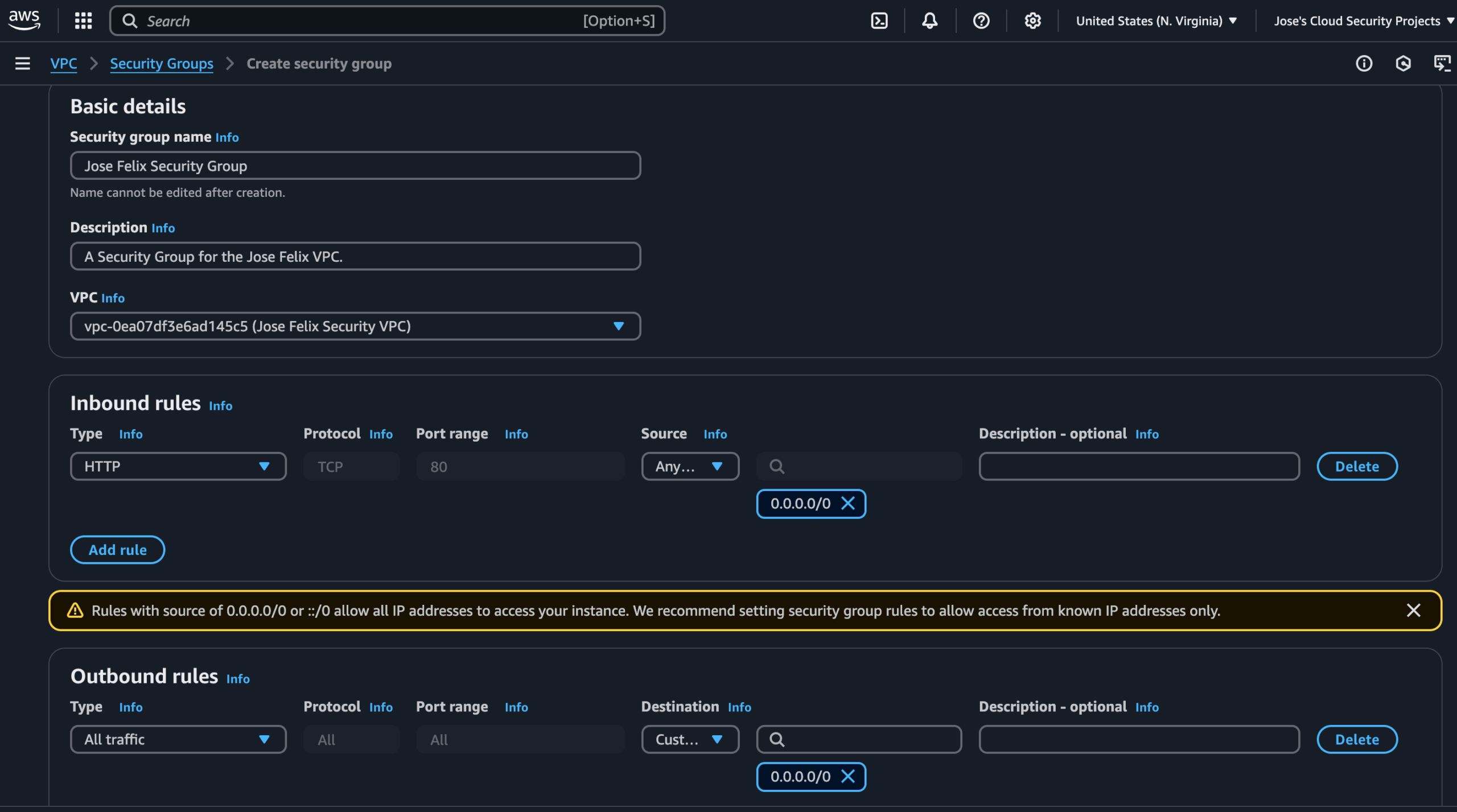
Security groups act as virtual firewalls operating at the resource level (not VPC or subnet level). They control what traffic can enter or leave specific resources based on protocols, port numbers, and IP addresses.
I configured inbound rules to allow HTTP traffic (port 80) from Anywhere-IPv4 (0.0.0.0/0), which means any IP address on the internet can send HTTP requests to resources using this security group. For outbound traffic, I kept the default rule allowing all outbound traffic to any destination.
Security Application:
Security groups provide a stateful packet filtering mechanism, automatically allowing return traffic for allowed connections. This simplifies security management while maintaining effective control.
Step 3: Setting Up Network ACLs
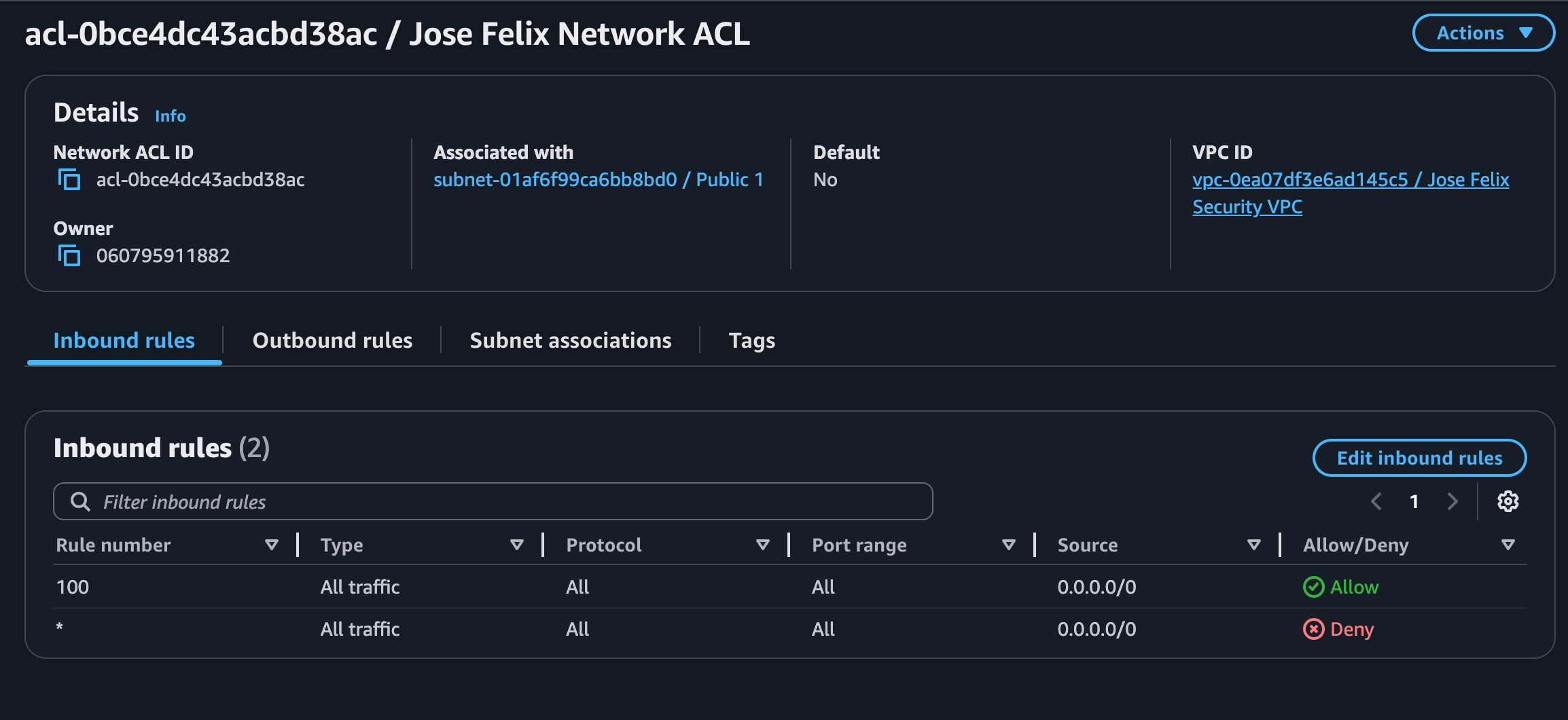
Network ACLs are traffic control mechanisms that operate at the subnet level in a VPC. They function like traffic cops stationed at every entry and exit point of a subnet, examining data packets against a set of rules before allowing them to pass through.
I experimented with both default and custom network ACLs:
- Default ACLs allow all traffic, with rule 100 permitting all inbound and outbound communication
- Custom ACLs begin with a “deny all” rule, requiring explicit allow rules for specific traffic types
Security Application:
Network ACLs provide stateless packet filtering, requiring explicit rules for both inbound and outbound traffic. They offer a complementary security layer to security groups, providing defense-in-depth for network security.
Step 4: Multi-Region Deployment with CloudShell
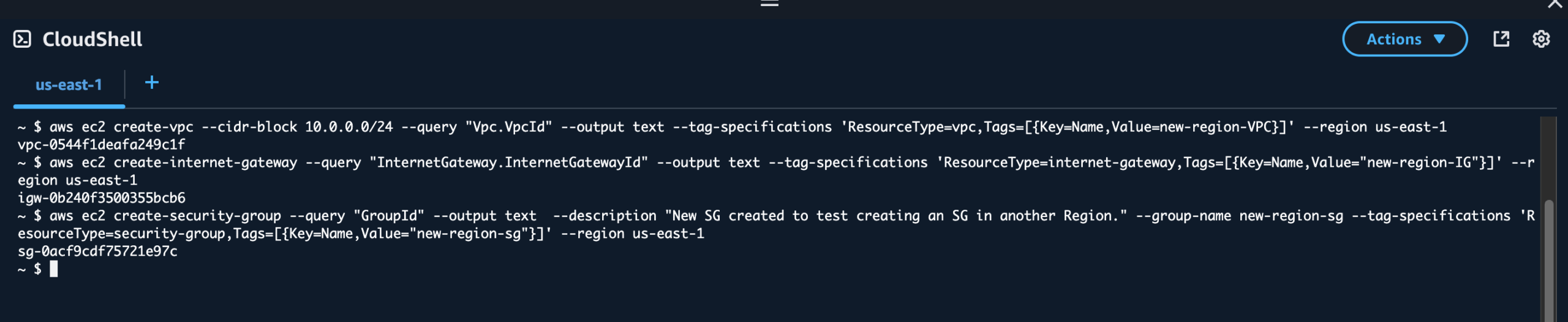
I created additional VPC resources using AWS CLI in CloudShell instead of the console, deploying them in a different region. I deployed three resources:
- A VPC with CIDR block 10.0.0.0/24 named “new-region-VPC” (vpc-0544f1deafa249c1f)
- An Internet Gateway named “new-region-IG” (igw-0b240f3500355bcb6)
- A Security Group named “new-region-sg” for controlling access to resources (sg-0acf9cdf75721e97c)
Teams often use multiple regions to improve latency for end users by placing resources closer to them geographically and to protect against regional outages or disasters.
Security Application:
Multi-region deployment enhances availability and disaster recovery capabilities while adding complexity to security management. Using CloudShell for consistent deployment helps maintain security standards across regions.
Step 5: Using EC2 Global View
EC2 Global View is a tool that provides a consolidated view of EC2 and VPC resources across all AWS regions from a single dashboard. I used it to find and manage my resources across different regions without having to manually switch between them.
I could narrow down my search by specific resource types like VPCs, security groups, or EC2 instances, viewing them as a consolidated list regardless of which region they were deployed in. This tool significantly improved efficiency compared to manually switching between regions.
Security Application:
EC2 Global View enables comprehensive security audits across regions, helping identify misconfigurations, unauthorized resources, or security group inconsistencies that might otherwise be missed in a complex multi-region deployment.
Network Security Principles Demonstrated
This project demonstrated several key networking security concepts that are essential for cloud environments:
Defense in Depth
Using multiple security controls (route tables, security groups, and network ACLs) provides layered protection, ensuring that if one security mechanism fails, others still provide protection.
Stateful vs. Stateless Filtering
Security groups provide stateful inspection (automatically allowing return traffic), while network ACLs offer stateless filtering (requiring explicit rules for both directions), creating complementary security mechanisms.
Least Privilege Access
Configuring security groups to allow only necessary traffic (like HTTP on port 80) implements the principle of least privilege, minimizing the attack surface for resources.
Centralized Management
Using EC2 Global View for monitoring resources across regions demonstrates the importance of centralized visibility for effective security governance in distributed environments.
Challenges and Solutions
Understanding Component Interactions
Challenge: One thing I didn’t expect was how the different network components interact with each other in a hierarchical way. Understanding the layered approach to security with both security groups and network ACLs was particularly challenging.
Solution: I created diagrams to visualize how traffic flows through the different security layers, which helped me understand the sequence of security evaluations and how they complement each other.
Multi-Region Resource Management
Challenge: Managing resources across multiple regions initially seemed complex and potentially error-prone, especially when trying to maintain consistent security configurations.
Solution: I leveraged EC2 Global View to gain centralized visibility and used CloudShell with parameterized scripts to ensure consistent deployment across regions, helping maintain security standards.
Key Takeaways and Best Practices
This project provided valuable insights into AWS network security:
- Layered Security Approach: Use route tables, security groups, and network ACLs together for comprehensive protection
- Understand Control Levels: Security groups operate at the resource level while network ACLs function at the subnet level
- Leverage Complementary Controls: Combine stateful security groups with stateless network ACLs for defense-in-depth
- Automate Deployment: Use CloudShell for consistent multi-region implementations
- Centralize Monitoring: Implement EC2 Global View for comprehensive security oversight
- Document Dependencies: Clearly map how security components interact to avoid misconfigurations
Cost Management Tip
While route tables, security groups, and network ACLs have no direct costs, they affect how traffic flows, which can impact data transfer costs. Be mindful of cross-region data flows which have higher transfer rates than intra-region communication.
What’s Next?
Building on this network security foundation, my upcoming projects will explore:
- Implementing VPC Endpoints for secure AWS service access
- Setting up VPN connections for secure remote access
- Creating Transit Gateways for inter-VPC communication
- Implementing AWS Network Firewall for advanced traffic inspection
- Configuring AWS Shield and WAF for DDoS and application protection
Each of these projects will build upon the security foundation established through proper VPC traffic management to ensure comprehensive protection for cloud resources, much like the cybersecurity risk assessment framework I developed previously.
Conclusion
Implementing proper traffic flow and security controls within AWS VPCs was a valuable learning experience that demonstrated the importance of layered security in cloud environments. The ability to control traffic at multiple levels with complementary security mechanisms provides the foundation for a robust security architecture.
As a US Navy veteran transitioning into Cloud Security, I found this project particularly relevant because it mirrors military defense strategies: creating multiple security perimeters, implementing checkpoint controls, and establishing clear communication channels. These universal security concepts translate perfectly to cloud environments.
Have you implemented advanced VPC security controls in your AWS environment? What challenges did you encounter with traffic management? Let me know in the comments below!
Stay tuned for my upcoming projects as I continue building expertise in AWS networking and security services.






