Hey there! If you’ve ever felt overwhelmed trying to figure out where to start with cybersecurity for your business, you’re not alone. Trust me, most companies struggle with this exact problem. That’s why I’ve put together this guide on creating a cybersecurity risk assessment that actually makes sense.
I’m going to walk you through the entire process using a fictional company called TechSecure Solutions as our example. By the end of this post, you’ll have a clear roadmap for identifying and addressing the security risks that matter most to your organization. Let’s dive in!
What’s a Cybersecurity Risk Assessment Anyway?
Think of a cybersecurity risk assessment as your security reality check. It’s basically asking three key questions:
- What could go wrong? (the bad stuff)
- How likely is it to happen? (probability)
- How bad would it be if it did? (impact)
It’s kind of like how you assess risks in your personal life. You probably don’t worry too much about a meteor hitting your house (super unlikely!), but you might be concerned about someone breaking in (more possible), so you lock your doors.
Building Your Risk Framework
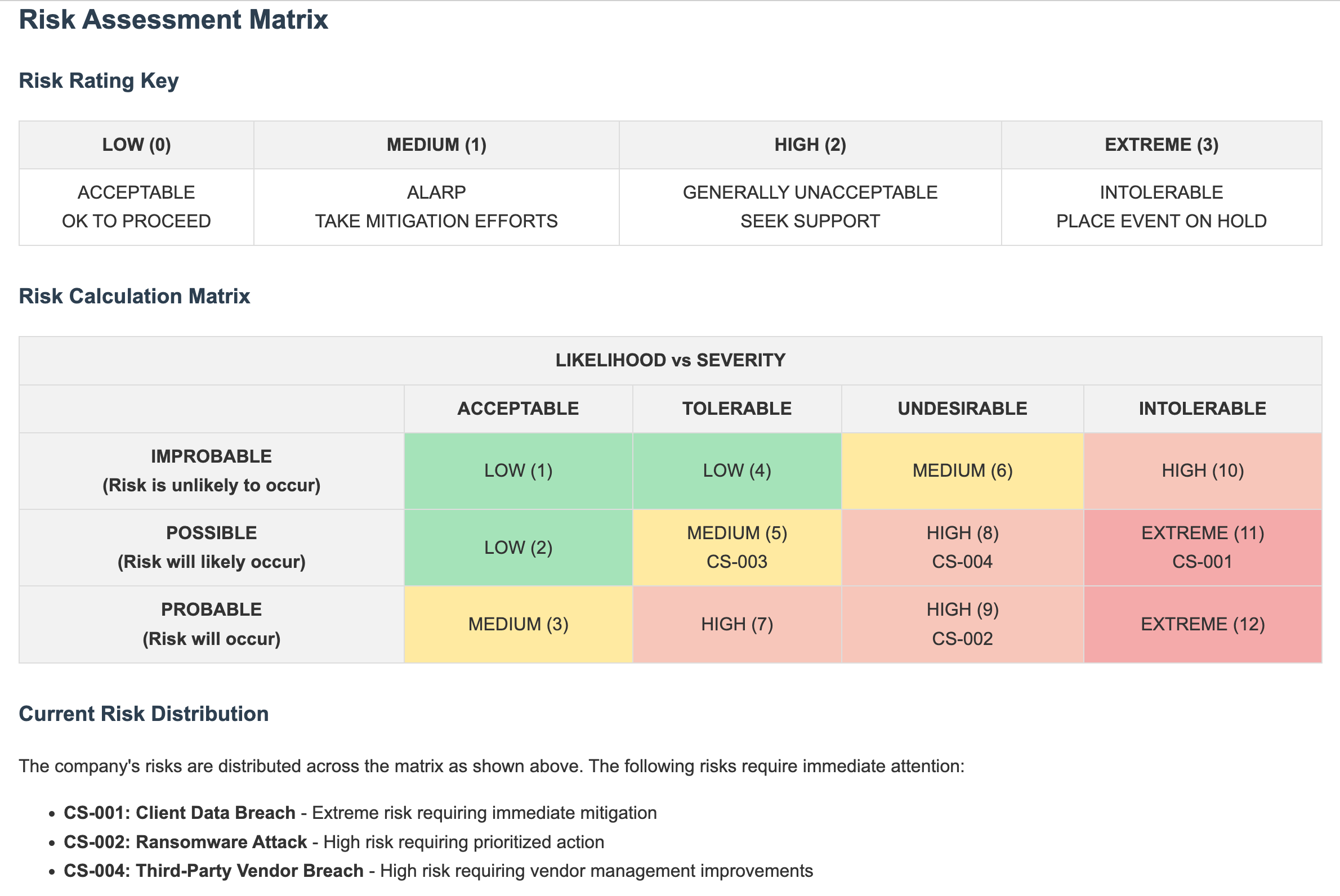
Before jumping in, we need a way to classify risks. I like to use a straightforward system:
- Low risk: Basically “we’re good” – proceed normally
- Medium risk: “Let’s keep an eye on this” – some mitigation needed
- High risk: “Houston, we have a problem” – needs significant attention
- Extreme risk: “Red alert!” – drop everything and fix this now
The beauty of this approach is that it combines how likely something is to happen with how bad it would be if it did. This helps you figure out where to focus your limited time and resources.
Step 1: Know Your Company
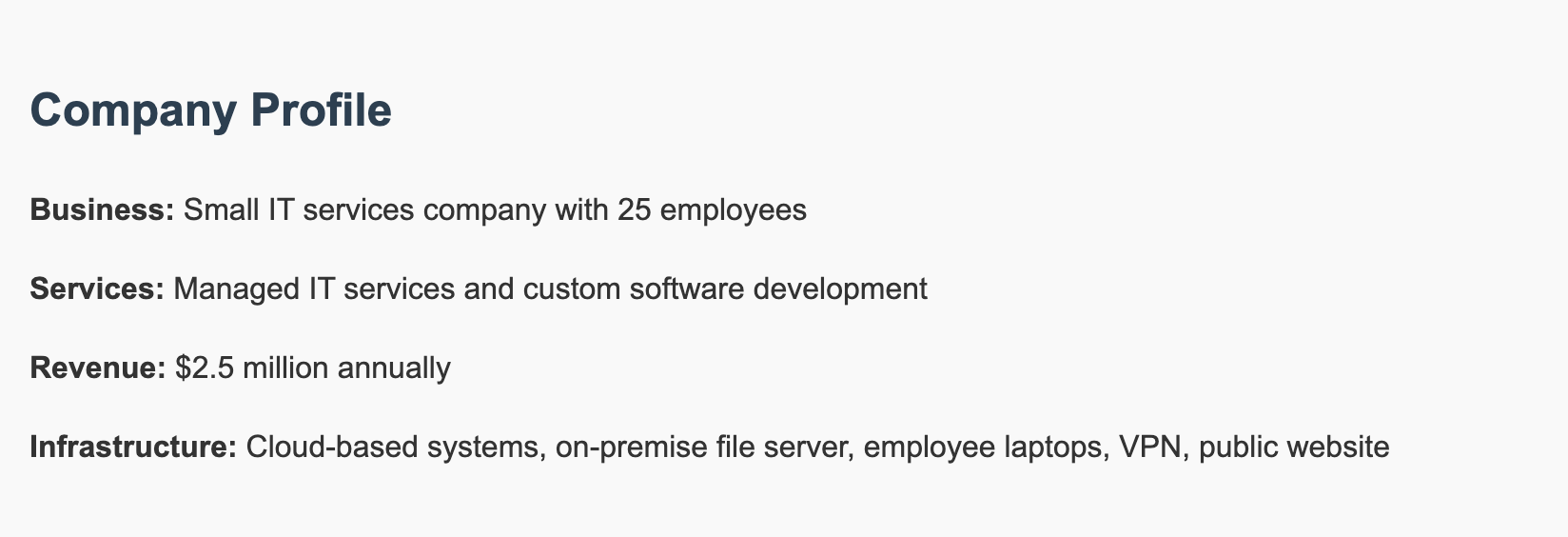
You can’t protect what you don’t understand, right? So first, let’s gather some basic info about your company:
For our example, TechSecure Solutions is a small IT services company with 25 employees. They handle client data, develop custom software, and have a mix of cloud services and on-premise systems. They’re successful but don’t have a dedicated security team—sound familiar?
Step 2: Identify What Could Go Wrong
This is where we brainstorm potential security nightmares. Don’t worry about being right away—start with what keeps you up at night.
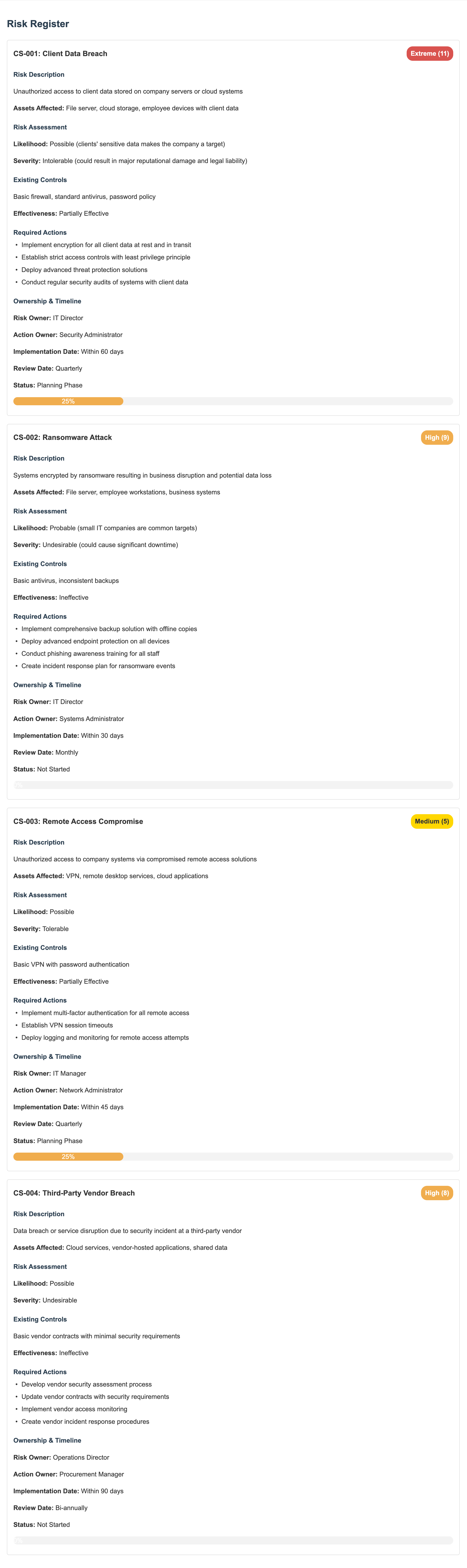
For TechSecure, their biggest concerns include:
- Client data being stolen (reputation killer!)
- Getting hit with ransomware (business stopper!)
- Someone hacking in through their VPN (sneaky backdoor!)
- A vendor they work with getting breached (supply chain nightmare!)
For each risk, write down a brief description and note which systems or data would be affected. Don’t overthink this part—just get your concerns on paper.
Step 3: How Bad Is It, Really?
Now for each risk, let’s figure out:
- How likely is this? Let’s be honest—is this something that happens all the time in your industry? Has it nearly happened to you before?
- How bad would it be? Would it be a minor inconvenience or a business-ending catastrophe?
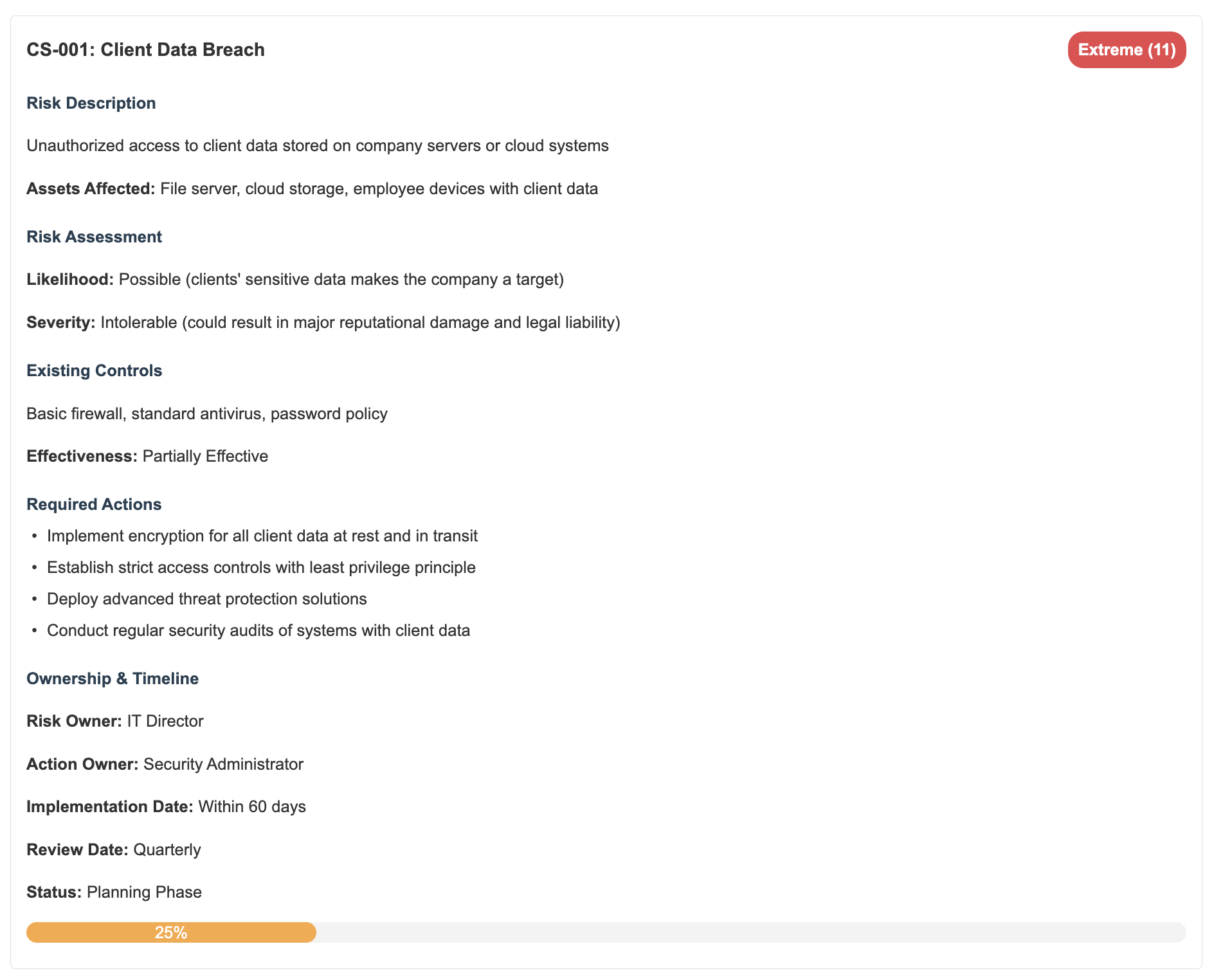
For example, TechSecure rated a client data breach as “Possible” (competitors have experienced it) and “Intolerable” (it could destroy client trust and possibly the business). That makes it an Extreme risk with a score of 11—definitely something they need to address ASAP.
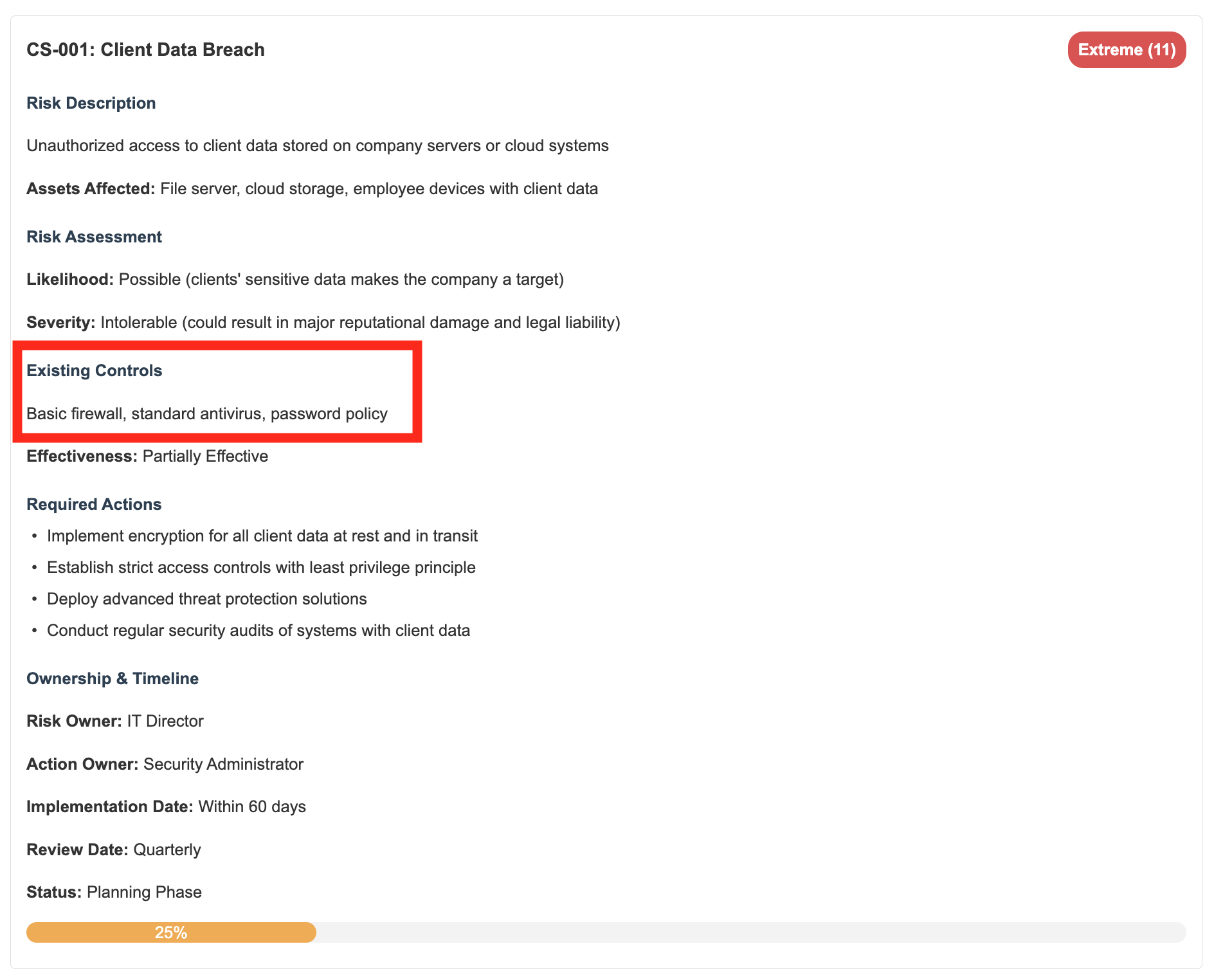
Step 4: What Are You Already Doing About It?
Before planning new security measures, take stock of what you already have in place. This prevents duplicate efforts and helps identify the real gaps.
TechSecure already has basic firewalls and password policies, but they’ve realized these controls are only “Partially Effective” against sophisticated attacks. Knowing this helps them focus on what to improve.
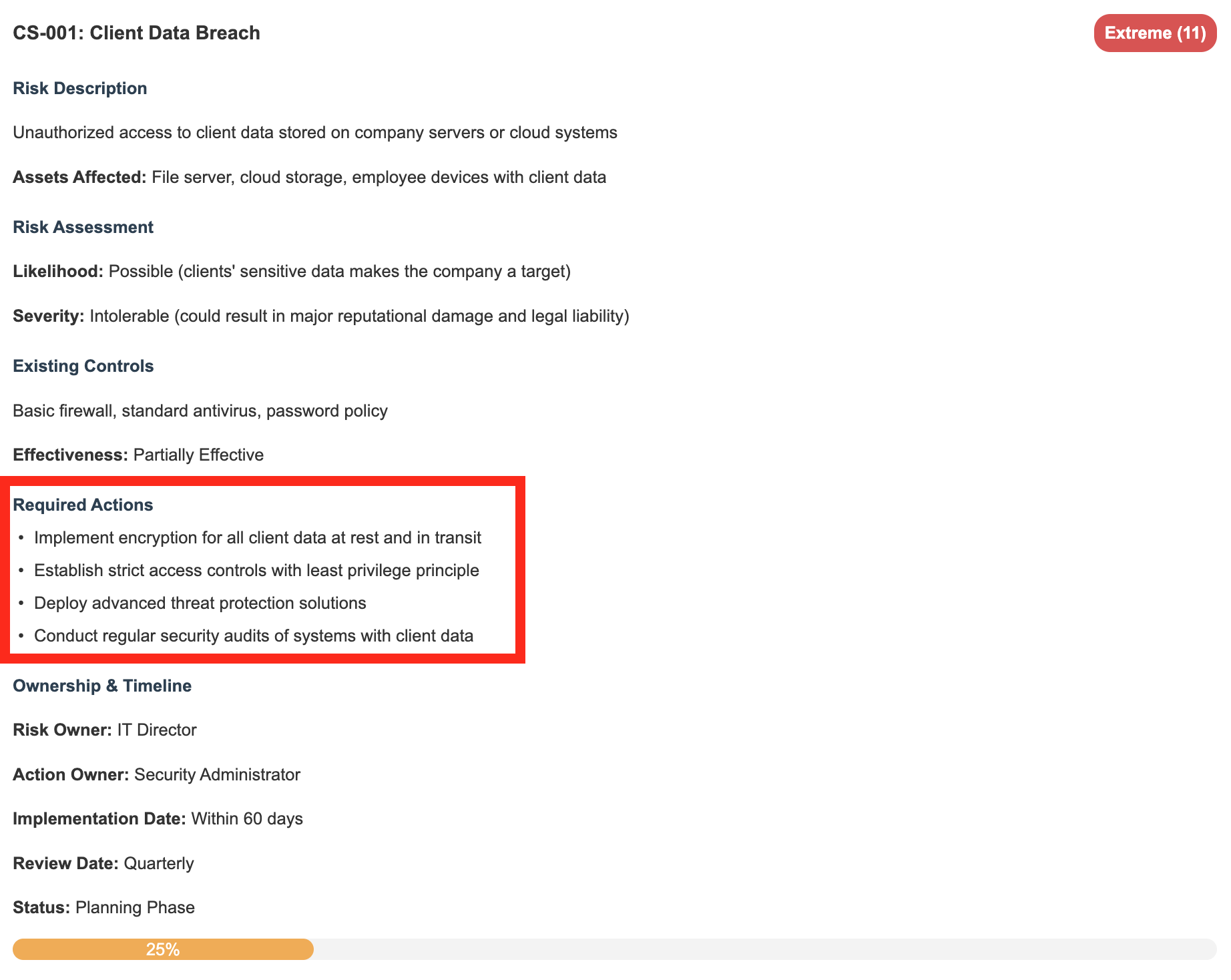
Step 5: Your Game Plan for Each Risk
For each risk, you need to decide your approach:
- Accept it: “We’ll take our chances” (only for truly low risks!)
- Mitigate it: “Let’s reduce this risk” (most common)
- Transfer it: “Let’s get insurance for this”
- Avoid it: “Let’s not do this risky thing at all”
Then list the specific actions you’ll take. For TechSecure’s ransomware risk, they decided to implement better backups, deploy advanced endpoint protection, and train staff to spot phishing attempts.
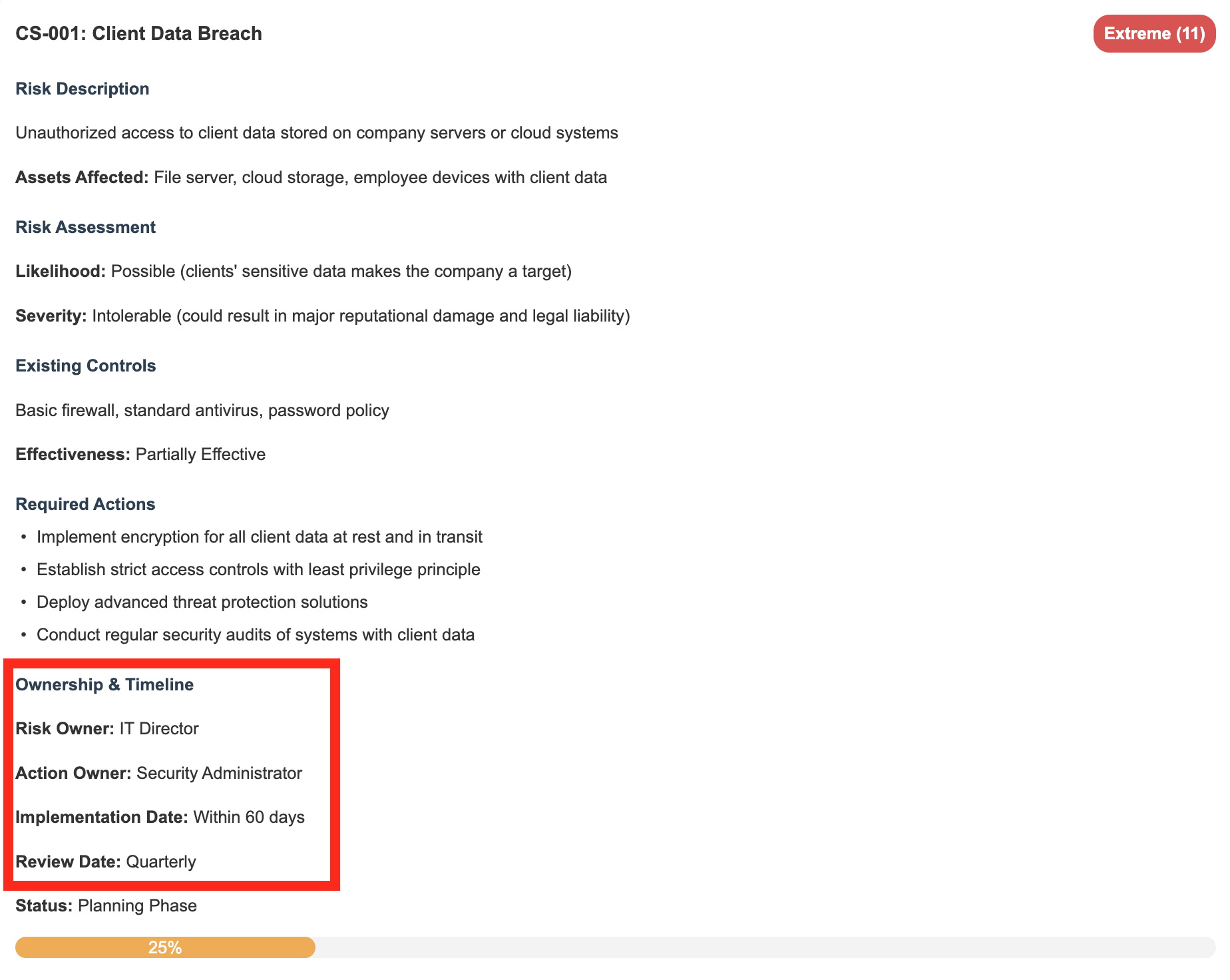
Step 6: Who’s Handling This and When?
The quickest way to ensure nothing gets done is to make it everyone’s responsibility. Instead, assign specific people to each risk and set deadlines:
- Who’s ultimately responsible for this risk? (the risk owner)
- Who’s going to implement the fixes? (the action owner)
- When does this need to be done? (implementation date)
- How often should we check on this? (review frequency)
TechSecure assigned their ransomware protection to their Systems Administrator with a 30-day deadline, knowing this was a high-priority item.
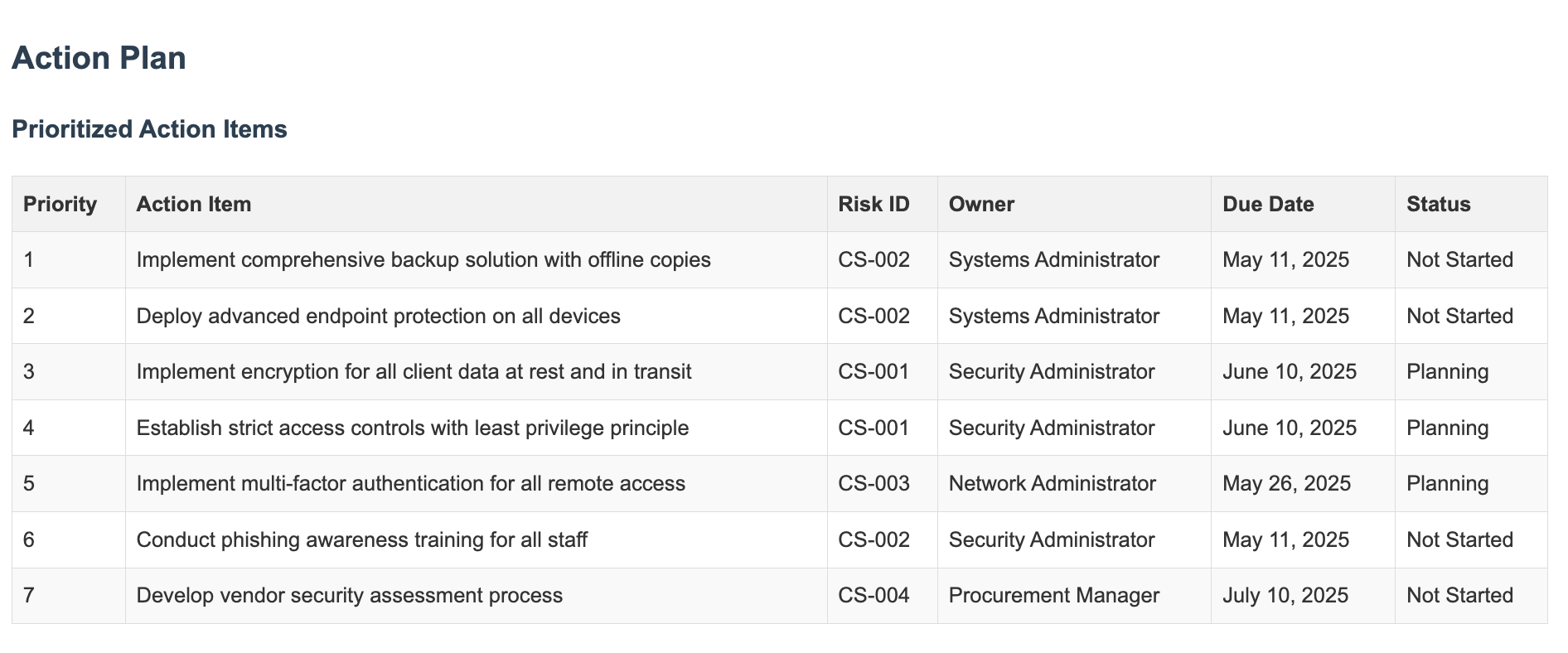
Step 7: Priorities, People!
Unless you have unlimited resources (and who does?), you can’t fix everything at once. Create a prioritized list based on:
- Which risks could cause the most damage
- What you can realistically tackle first
- What dependencies exist (some fixes might need to happen before others)
TechSecure prioritized implementing backups immediately because it was both critical and relatively straightforward.
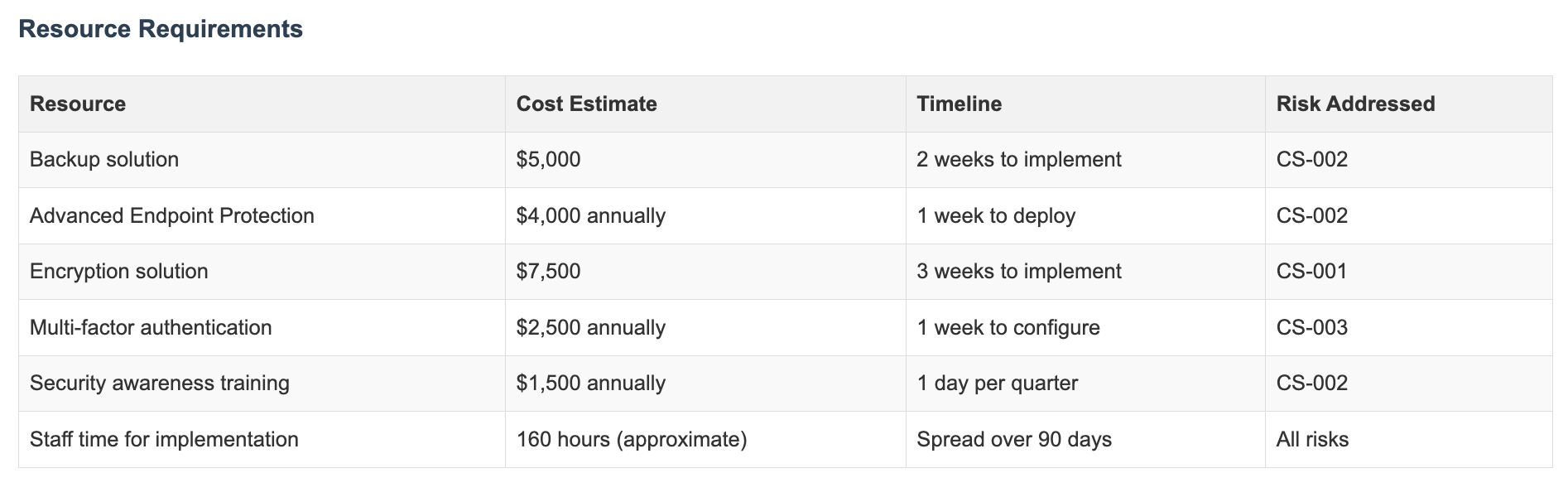
Step 8: What Will It Take?
Let’s get real about resources. Security isn’t free, and pretending it is leads to half-implemented solutions that don’t actually work.
Document what you’ll need:
- Budget for tools and services
- People’s time
- Training
- Outside expertise (if needed)
TechSecure calculated they needed about $5,000 for a backup solution, $4,000 for endpoint protection, and significant staff time to implement everything properly.
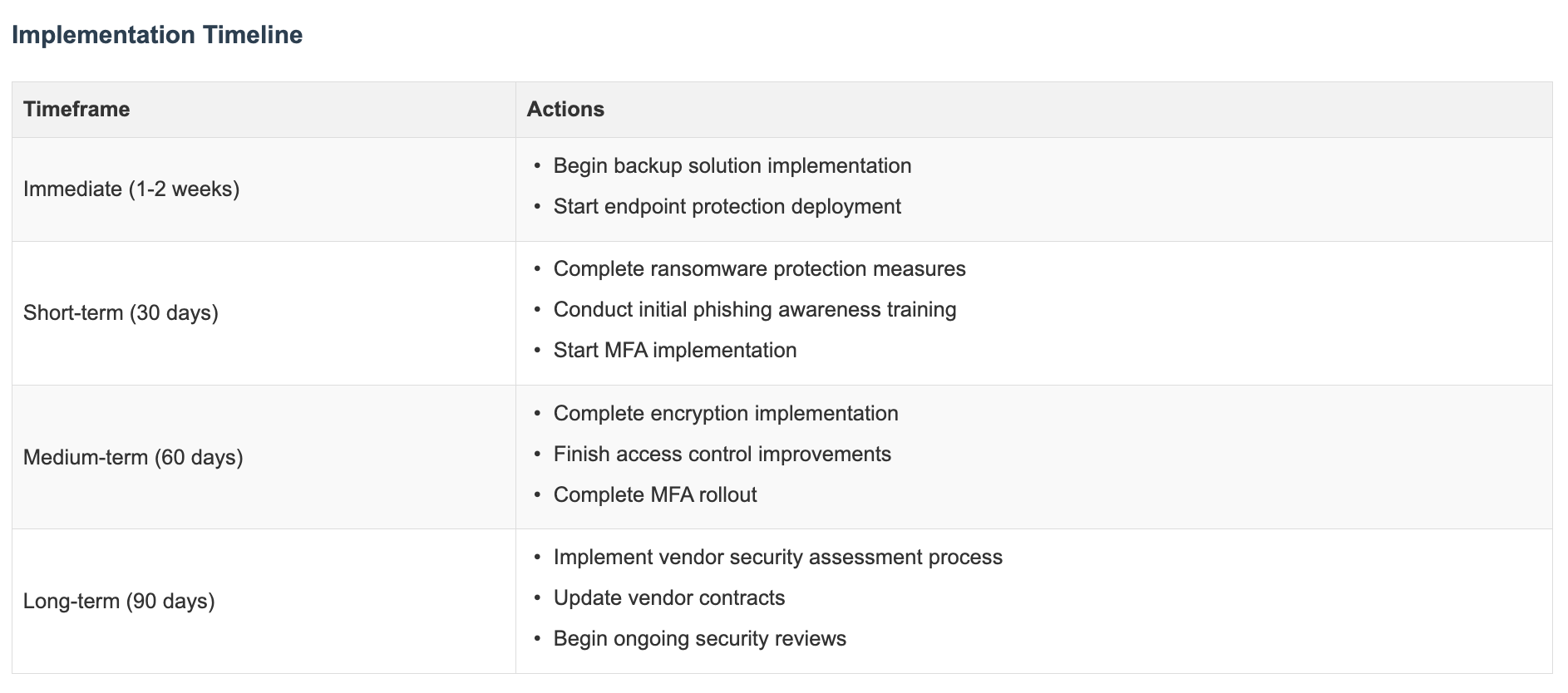
Step 9: Breaking It Down Into Manageable Chunks
Rome wasn’t secured in a day! Break your plan into time phases:
- Right now (1-2 weeks)
- Soon (30 days)
- This quarter (90 days)
- Longer-term (beyond 90 days)
This makes the whole thing less overwhelming and helps you track progress. TechSecure focused first on backups and endpoint protection, knowing these would give them the biggest security boost for their effort.
Step 10: This Isn’t a “Set It and Forget It” Thing
Security is never “done.” Set up regular check-ins to:
- Review how your controls are working
- Assess if risk levels have changed
- Identify new risks that have emerged
- Adjust your plans accordingly
TechSecure decided to review their highest risks monthly and the others quarterly, with a full reassessment annually.
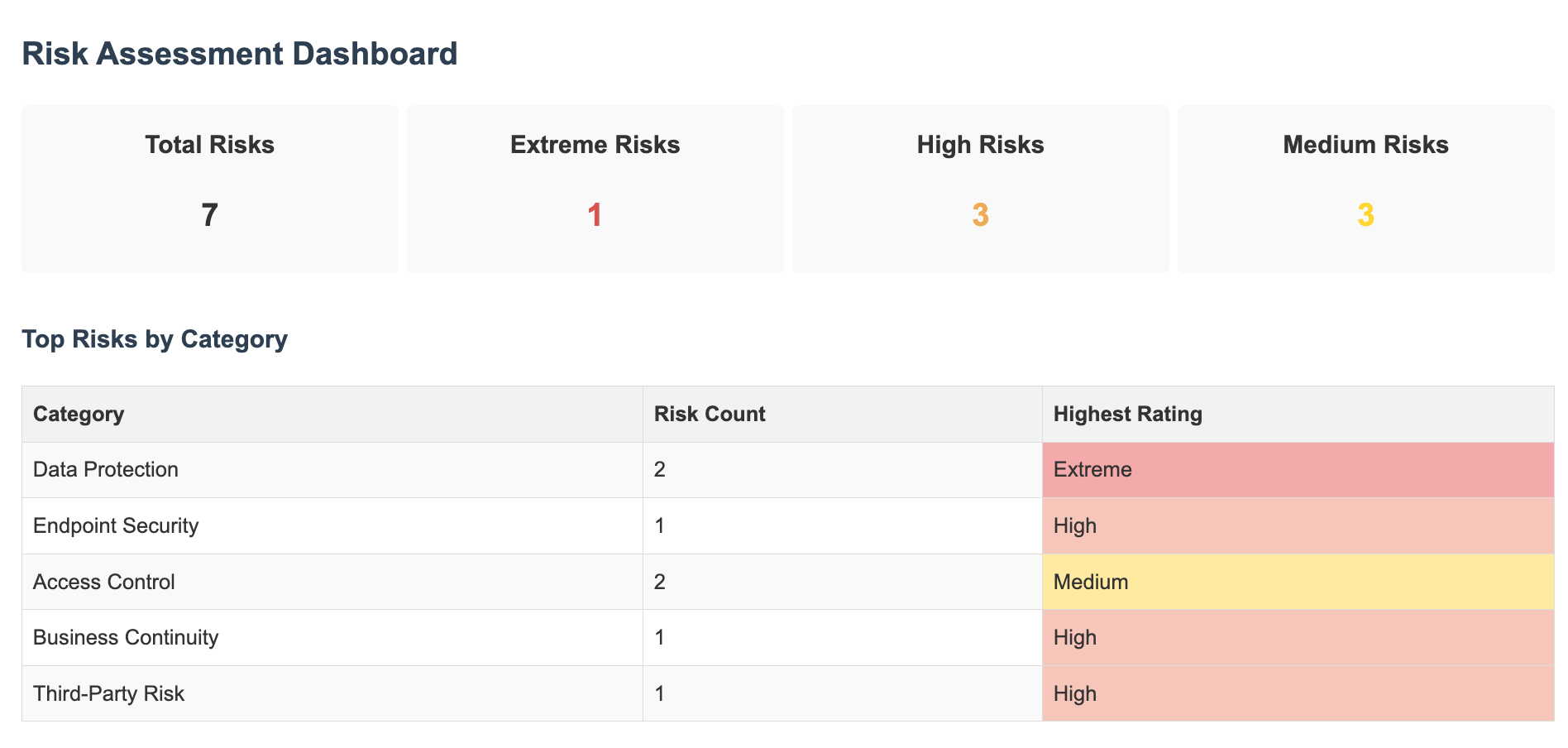
Your Security Command Center
A dashboard gives you that quick “state of security” overview that’s perfect for both technical teams and executives. At a glance, you can see:
- How many high-risk items need attention
- What progress you’re making on fixes
- Which areas of your business have the most risk
This helps keep security visible and top-of-mind for everyone.
Common Risks You Should Probably Look At
While every business is unique, these are the usual suspects I see across most organizations:
- Data Protection: Is your sensitive information locked down?
- Endpoint Security: Are your computers and devices protected from malware?
- Access Control: Who can get into your systems, and should they?
- Network Security: Is your network properly defended?
- Third-Party Risk: Are your vendors and partners creating risk for you?
- Business Continuity: Can you recover when (not if) something goes wrong?
- Human Factors: Are your people equipped to be part of your security solution?
Most security incidents trace back to weaknesses in these areas, so they’re good places to start your assessment.
Wrapping Up
I know security can feel overwhelming, especially when you’re already juggling a million other business priorities. But I hope this guide shows that a thoughtful, structured approach makes it manageable.
Remember, perfect security doesn’t exist—but significant improvement is absolutely within your reach. Start with your biggest risks, make steady progress, and you’ll dramatically reduce your chances of becoming the next security headline.
Have questions about assessing your security risks? Drop them in the comments below!






