Introduction
As I continue building my cloud security skillset, I’ve been focusing on foundational AWS networking services that form the backbone of secure cloud infrastructure. One of the most essential services is AWS Virtual Private Cloud (VPC), which provides an isolated network environment within the AWS cloud.
In this blog post, I’ll share my experience creating a secure, isolated network environment in AWS. Building on my previous projects, from implementing secure access management with AWS IAM, creating interactive dashboards with QuickSight, to hosting static websites on S3—this VPC implementation represents the next logical step in my AWS journey, focusing on network security fundamentals.
I established a VPC with a specific CIDR block, created a subnet within that network range, and attached an internet gateway to allow controlled connectivity. I implemented this using both the AWS Management Console and AWS CloudShell with CLI commands, comparing the advantages of each approach. This network foundation will support future security implementations, much like the cybersecurity risk assessment framework I developed previously.
Project Overview
Time Investment:
Approximately 2 hours (including initial setup, CloudShell experimentation, and cleanup)
AWS Services Used:
- Amazon Virtual Private Cloud (VPC)
- Subnets
- Internet Gateway
- AWS CloudShell
Key Concepts Learned:
- VPC and subnet creation
- CIDR block configuration
- Internet gateway implementation
- Availability Zone placement
- CLI vs Console deployment approaches
- Resource dependency management
Why AWS VPC is Fundamental to Cloud Architecture
Before diving into implementation, here’s why VPC is considered the foundation of AWS networking:
- Network Isolation: Create private, logically isolated sections of AWS
- Security Control: Define network topology and traffic flow
- Connectivity Options: Configure public, private, and hybrid connectivity
- Availability and Redundancy: Span resources across multiple Availability Zones
- Cost Optimization: Control data transfer paths to manage costs
Step 1: Understanding Virtual Private Clouds
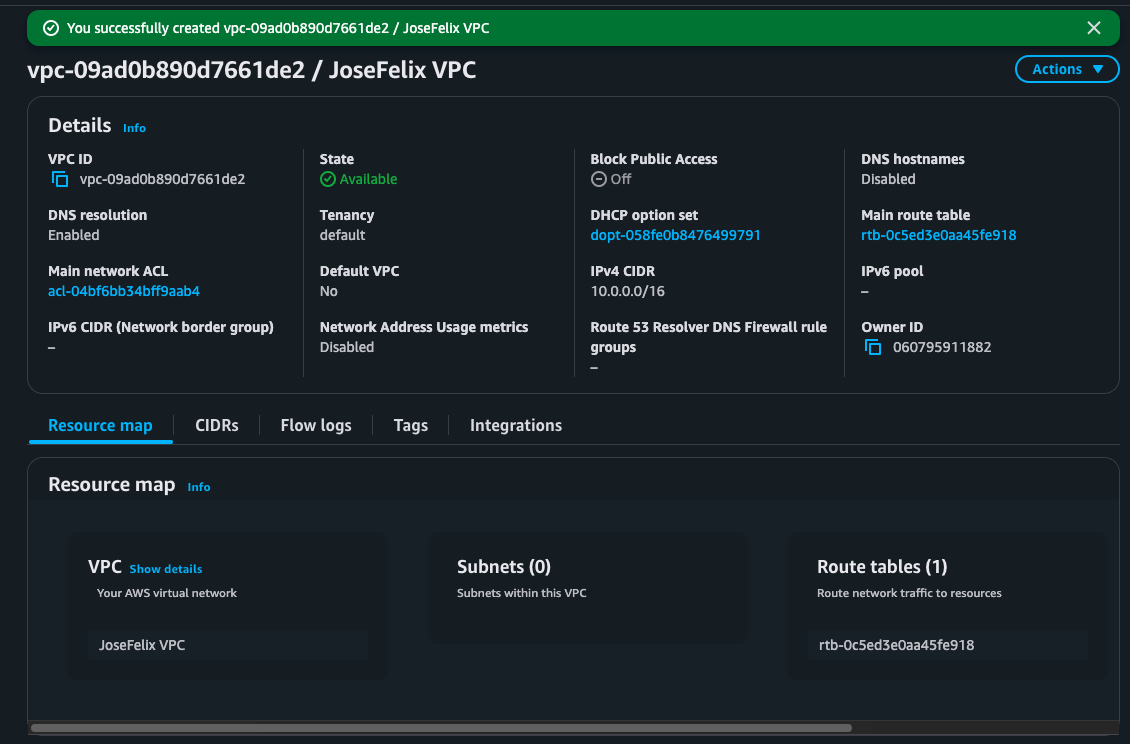
Virtual Private Clouds (VPCs) are isolated sections of AWS where you build your digital infrastructure with complete control. I created my VPC with a CIDR block of 10.0.0.0/24, which provided 256 possible IP addresses for my resources.
When specifying a CIDR block, the notation (the /24 part) determines how many IP addresses are available – the smaller the number after the slash, the larger the pool of addresses. For instance, a /16 block would provide 65,536 addresses, while my /24 block is more targeted for my needs.
Security Impact:
VPCs provide network isolation, which is a fundamental security principle in cloud environments. This isolation helps prevent unauthorized access and creates clear security boundaries between different applications or environments.
Step 2: Creating a Subnet
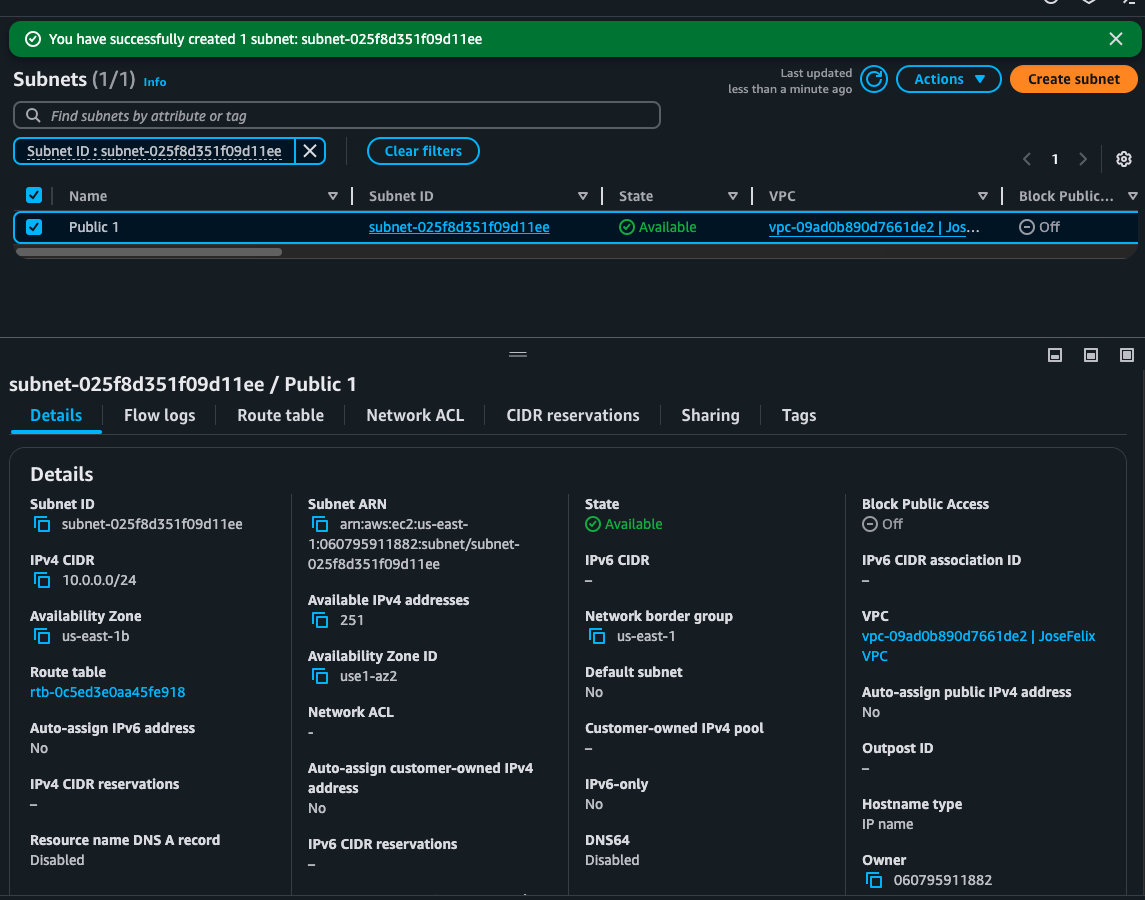
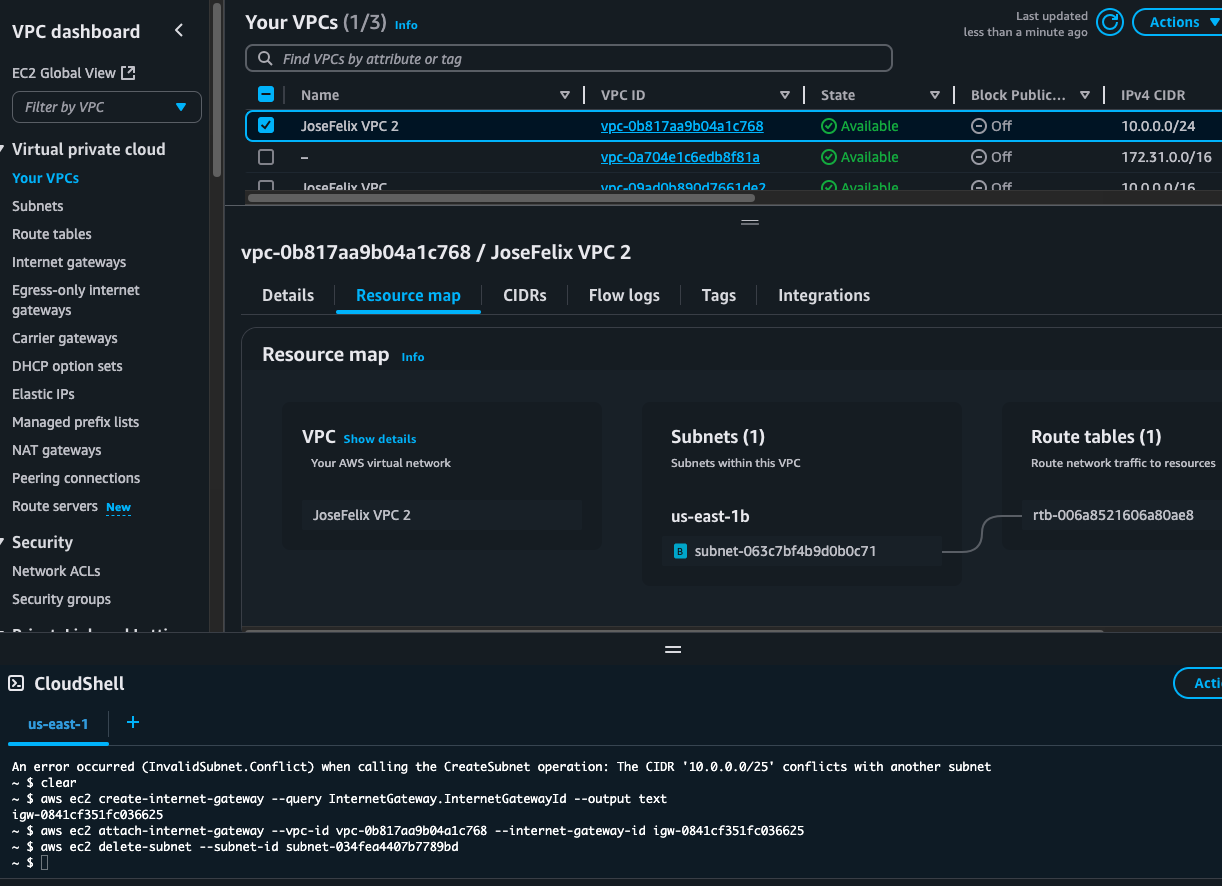
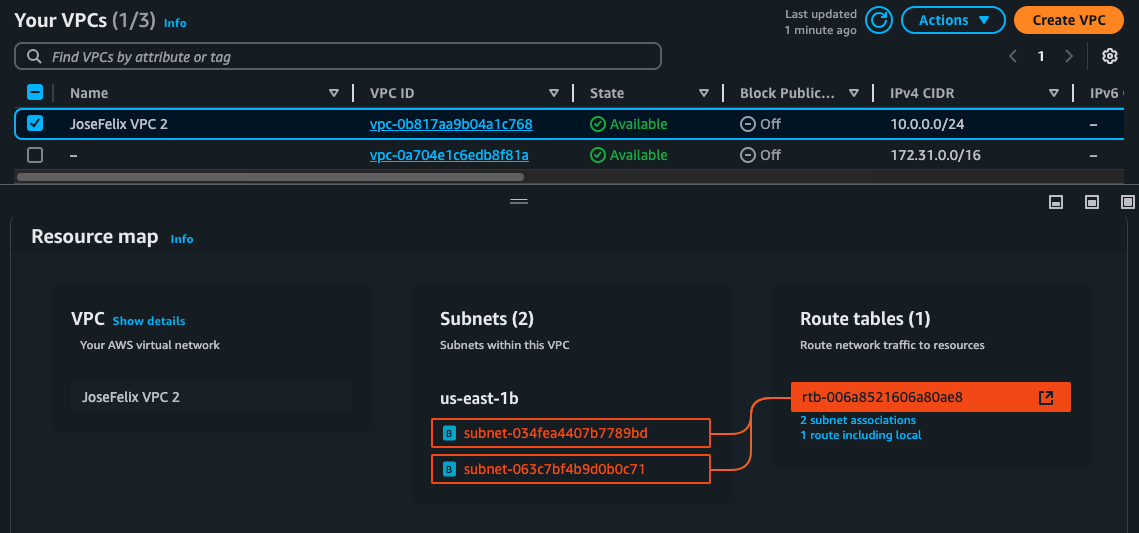
Within my VPC, I created a subnet using a CIDR block of 10.0.0.0/24, which utilizes the full range of IP addresses available in my VPC. This subnet exists in a specific Availability Zone (us-east-1b as shown in the screenshot), which helps with fault tolerance by allowing resources to be spread across multiple physical data centers.
After creating the subnet, I configured it as a public subnet with the “Block Public Access” setting turned off. This configuration, along with the proper route table settings, allows resources in this subnet to communicate with the internet.
Key Configuration Details:
- CIDR Block: 10.0.0.0/24 (providing 256 addresses)
- Availability Zone: us-east-1b
- Block Public Access: Off
- Route Table: rtb-0c5c03e0aa45fe918
Security Application:
Subnets allow for network segmentation, enabling the creation of both public areas (for internet-facing resources) and private areas (for protected resources) within a VPC. This segmentation is a key security control for limiting exposure of sensitive systems.
Step 3: Attaching an Internet Gateway
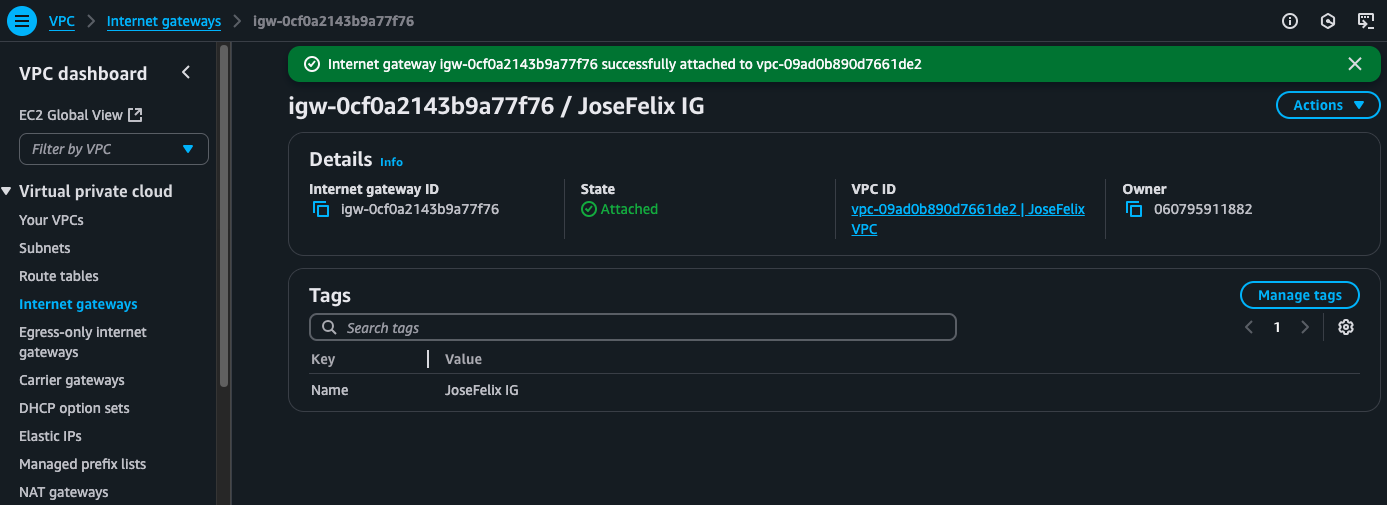
Internet gateways are specialized AWS components that connect a VPC to the internet, functioning like a highway entrance/exit between a private cloud network and the public internet. I attached an internet gateway to my VPC, creating a path for two-way communication between my cloud resources and the outside world.
This connection is essential for hosting public-facing applications like websites, allowing API access, or letting EC2 instances download updates. The internet gateway serves as the bridge between my private cloud network and the public internet.
Security Impact:
Internet gateways provide controlled external connectivity. Without properly configured routes and security groups, even resources with public IPs remain inaccessible, providing defense-in-depth security architecture.
Step 4: Using AWS CloudShell for Rapid Deployment
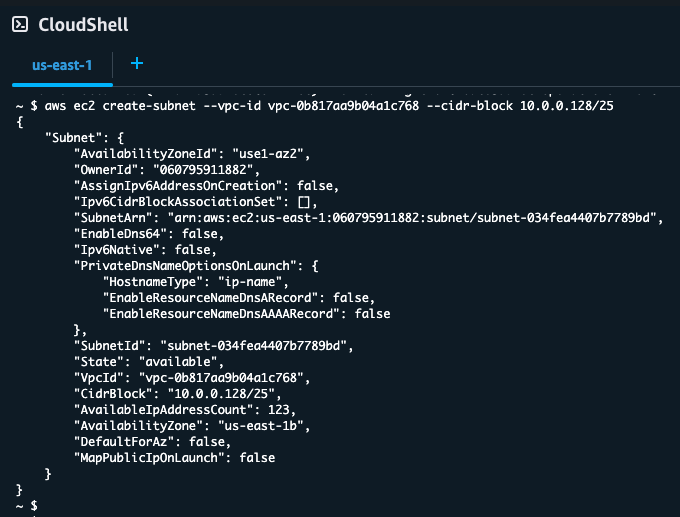
As part of a special exercise, I used AWS CloudShell to deploy VPC resources using the command line. CloudShell is a browser-based shell environment with AWS CLI pre-installed, accessible directly from the AWS Management Console.
I executed various CLI commands to create VPCs and subnets with different CIDR blocks. For instance, I created a subnet with a more specific CIDR block of 10.0.0.128/25, which allocates 128 IP addresses within my VPC:
aws ec2 create-subnet --vpc-id vpc-0b817aa9b04a1c768 --cidr-block 10.0.0.128/25
The command returned detailed information about the subnet, including:
- Subnet ID: subnet-034fed4407b7789bd
- Availability Zone: us-east-1b
- Available IP Address Count: 123 (of 128 total addresses, as AWS reserves 5 addresses in each subnet)
I also experimented with creating a subnet using the full VPC CIDR range:
aws ec2 create-subnet --vpc-id vpc-0b817aa9b04a1c768 --cidr-block 10.0.0.0/24
Additionally, I worked with tagging resources to maintain proper organization:
aws ec2 create-tags --resources vpc-0b817aa9b04a1c768 --tags Key=Name,Value="JoseFelix VPC"
What I found particularly interesting was how the CLI returned the full resource details in JSON format, providing complete visibility into all the properties and settings of the created resources. This feedback is extremely valuable for validation and scripting purposes.
While I did encounter some syntax errors during my experimentation with the AWS CLI (as shown in the later screenshots), these provided valuable learning opportunities about the precise command structure required for AWS CloudShell operations.
Console vs. CLI Approach:
| AWS Console Advantages | AWS CLI Advantages |
|---|---|
| Visual interface helps understand relationships | Speed and efficiency with fewer commands |
| Reduces syntax errors with guided workflows | Create reusable scripts for consistent deployments |
| Provides immediate feedback | Automation capabilities |
| Clearly shows component connections | Eliminates need to navigate multiple screens |
The CloudShell experience demonstrated how infrastructure as code principles can be applied even for basic networking components, allowing for more consistent and reproducible deployments.
Step 5: Managing Resource Deletion
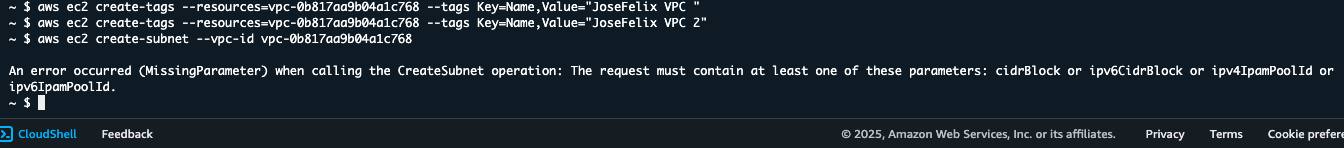
When cleaning up my VPC resources, I discovered the dependency hierarchy that exists between AWS networking components. Resources had to be deleted in a specific order, requiring me to detach the internet gateway from the VPC before I could delete it.
This revealed an important lesson about cloud resource management – that there’s a careful sequence required when dismantling infrastructure that isn’t immediately obvious when building it:
- Detach the internet gateway from the VPC
- Delete the internet gateway
- Delete the subnet
- Delete the VPC
Operational Insight:
In cloud environments, resource dependencies must be understood to prevent errors during infrastructure changes. This knowledge is essential for both building and decommissioning cloud resources safely.
Networking Fundamentals Demonstrated
This project demonstrated several key networking concepts that are essential for cloud security:
Network Isolation
VPCs create isolated network environments that act as security boundaries, reducing attack surface and minimizing the impact of potential breaches by limiting lateral movement.
Network Segmentation
Subnets allow for dividing the network into segments, enabling the separation of resources based on security requirements and restricting traffic flow between segments.
Controlled Internet Access
Internet gateways provide the ability to control which resources can access the internet, enabling public-facing applications while maintaining security for internal systems.
IP Address Management
CIDR notation and IP addressing strategies ensure efficient allocation and organization of IP addresses, providing structure and manageability to cloud networks.
Challenges and Solutions
Challenge 1: CIDR Block Configuration
Challenge:
One of the most difficult aspects was understanding and correctly configuring CIDR blocks for the VPC and subnet, especially ensuring the subnet CIDR was properly contained within the VPC CIDR range.
Solution:
I researched CIDR notation and practiced with different configurations, learning that a subnet’s CIDR needs to have a larger prefix (the number after the slash) and must fall completely within the VPC’s IP range.
Challenge 2: Resource Deletion Dependencies
Challenge:
When attempting to delete my VPC resources, I encountered dependency errors because resources had to be deleted in a specific order.
Solution:
I learned to detach the internet gateway from the VPC first, then delete the gateway, followed by the subnet, and finally the VPC itself. This experience taught me about the hierarchical nature of AWS resources.
Key Takeaways and Best Practices
This project provided valuable insights into AWS networking foundations:
- Start with Well-Planned CIDR Blocks: Properly plan your IP address space before creating VPCs and subnets
- Implement Network Segmentation: Use subnets to isolate resources based on function and security requirements
- Control Internet Access: Only expose resources to the internet that truly require external connectivity
- Understand Resource Dependencies: Be aware of the relationships between resources for proper management
- Consider Automation: Use CloudShell or AWS CLI for repeatable, consistent deployments
- Document Your Network Architecture: Maintain clear documentation of your network design for future reference
Cost Management Tip
VPC, subnets, and route tables are free, but you pay for resources like NAT gateways, VPN connections, and data transfer. Internet gateways are free to provision, but you’ll pay for data transferred through them.
Applying These Concepts to Security Architecture
This VPC implementation demonstrates several security architecture principles:
- Defense in Depth: Multiple network layers protect critical resources
- Segmentation: Separate networks contain different types of resources
- Controlled Connectivity: Explicit configuration of internet access
- Resource Isolation: Clear boundaries between different environments
Each of these principles contributes to a robust security posture that protects AWS environments from both external threats and internal misconfigurations.
What’s Next?
Building on this VPC foundation, my upcoming networking projects will explore:
- VPC Traffic Flow and Security with Route Tables and ACLs
- Creating Private Subnets for sensitive resources
- Launching and securing VPC resources
- Testing VPC connectivity across different resources
- Implementing VPC endpoints for secure AWS service access
Each of these projects will leverage the networking foundation established through VPC to ensure proper security and connectivity for cloud resources.
Conclusion
Creating a Virtual Private Cloud from scratch was a valuable learning experience that demonstrated the importance of network design in cloud environments. The ability to create isolated networks with controlled connectivity forms the foundation of AWS architecture.
As a US Navy veteran transitioning into Cloud Security, I found this project particularly relevant because it mirrors military security principles: establishing secure perimeters, controlling access points, and implementing defense-in-depth. These universal security concepts translate perfectly to cloud environments.
Have you implemented VPCs in your AWS environment? What challenges did you encounter with network design? Let me know in the comments below!
Stay tuned for my upcoming projects as I continue building expertise in AWS networking and security services.